Software documentation or source code documentation is written text that accompanies computer software. It either explains how it operates or how to use it, or may mean different things to people in different roles.
Documentation is an important part of software engineering. Types of documentation include:
• Architecture/Design - Overview of software. Includes, relations to an environment and construction principles to be used in design of software components.
• Technical - Documentation of code, algorithms, interfaces, and APIs.
• End User - Manuals for the end-user, system administrators and support staff.
• Marketing - Product briefs and promotional collateral.
Architecture/Design Documentation:
Architecture documentation is a special breed of design documents. In a way, architecture documents are third derivative from the code (design documents being second derivative, and code documents being first). These documents do not describe how to program a particular routine, or even why that particular routine exists in the form that it does, but instead merely lays out the general requirements that would motivate the existence of such a routine.
Technical Documentation:
This is what most programmers mean when using the term software documentation. When creating software, code alone is insufficient. There must be some text along with it to describe various aspects of its intended operation. It is important for the code documents to be thorough, but not so verbose that it becomes difficult to maintain them.
End User Documentation:
Typically, the user documentation describes each feature of the program, and assists the user in realizing these features. A good user document can also go so far as to provide thorough troubleshooting assistance. It is very important for user documents to not be confusing, and for them to be up to date.
Marketing Documentation:
For many applications it is necessary to have some promotional materials to encourage casual observers to spend more time learning about the product. One good marketing technique is to provide clear and memorable catch phrases that exemplify the point we wish to convey, and also emphasize the interoperability of the program with anything else provided by the manufacturer.
Wednesday, October 31, 2007
Tuesday, October 30, 2007
Updating System i5 for Daylight Saving time changes:
In the Energy Policy Act of 2005, Congress changed Daylight Saving Time (DST) in the United States so that starting this year (2007) DST begins three weeks earlier than it did last year, on the second Sunday of March. Conversely, 2007 will also see Daylight Saving Time end one week later than last year, on the first Sunday in November.
There are two ways to handle this change. You can do a manual adjustment or you can apply IBM's new Daylight Saving Time PTFs for i5 systems running i5/OS V5R3 and V5R4.
• For i5/OS V5R4, order PTFs SI26040 and SI25990
• For i5/OS V5R3, order PTFs SI26039 and SI25991
The PTFs automate the changes needed to support the new DST rules. After application, all of the time zone rules on the system will be updated to the new DST starting and ending dates.
After applying the PTF upgrade, you can check to see if the fix has been applied by performing the following steps on all your upgraded partitions:
1. Double-check the Time Zone description that your partition is using by referencing the QTIMZON system value. On a 5250 green screen, you can check this value by using this Display System Value command (DSPSYSVAL).
DSPSYSVAL SYSVAL(QTIMZON)
2. Look up the Daylight Saving Time start and end date for your time zone value by using the Work with Time Zone Descriptions command (WRKTIMZON). Run this command to display all Time Zone descriptions on your system, like this:
WRKTIMZON TIMZON(*ALL)
The Work with Time Zone Descriptions screen will display all the different time zones that are defined on your system.
To find your QTIMZON time zone on the WRKTIMZON screen, page down the list until you see either the time zone listed in QTIMZON or a time zone with a greater than sign (>) in front of it (the default time zone will always be designated in this list by a '>' sign). Place a 5=Display details in front of your default time zone entry and press Enter. On the screens that follow, you will see the starting and ending DST dates for your time zone description. What you are interested in is whether or not the PTFs changed your time zone DST start and end dates correctly.
If your time zone rule could not be changed by the PTF upgrade (as explained above), then you should change it manually by entering the following Change Time Zone Description command (CHGTIMZON) and pressing the F4 key.
CHGTIMZON TIMZON(TIME_ZONE_DESCRIPTION_NAME)
Locate the DST start and end dates on the second CHGTIMZON screen (which can be accessed by pressing the F24=More key on the first screen, followed by the F9=All key). If your time zone DST dates were not changed, you can change them manually from this screen.
There are two ways to handle this change. You can do a manual adjustment or you can apply IBM's new Daylight Saving Time PTFs for i5 systems running i5/OS V5R3 and V5R4.
• For i5/OS V5R4, order PTFs SI26040 and SI25990
• For i5/OS V5R3, order PTFs SI26039 and SI25991
The PTFs automate the changes needed to support the new DST rules. After application, all of the time zone rules on the system will be updated to the new DST starting and ending dates.
After applying the PTF upgrade, you can check to see if the fix has been applied by performing the following steps on all your upgraded partitions:
1. Double-check the Time Zone description that your partition is using by referencing the QTIMZON system value. On a 5250 green screen, you can check this value by using this Display System Value command (DSPSYSVAL).
DSPSYSVAL SYSVAL(QTIMZON)
2. Look up the Daylight Saving Time start and end date for your time zone value by using the Work with Time Zone Descriptions command (WRKTIMZON). Run this command to display all Time Zone descriptions on your system, like this:
WRKTIMZON TIMZON(*ALL)
The Work with Time Zone Descriptions screen will display all the different time zones that are defined on your system.
To find your QTIMZON time zone on the WRKTIMZON screen, page down the list until you see either the time zone listed in QTIMZON or a time zone with a greater than sign (>) in front of it (the default time zone will always be designated in this list by a '>' sign). Place a 5=Display details in front of your default time zone entry and press Enter. On the screens that follow, you will see the starting and ending DST dates for your time zone description. What you are interested in is whether or not the PTFs changed your time zone DST start and end dates correctly.
If your time zone rule could not be changed by the PTF upgrade (as explained above), then you should change it manually by entering the following Change Time Zone Description command (CHGTIMZON) and pressing the F4 key.
CHGTIMZON TIMZON(TIME_ZONE_DESCRIPTION_NAME)
Locate the DST start and end dates on the second CHGTIMZON screen (which can be accessed by pressing the F24=More key on the first screen, followed by the F9=All key). If your time zone DST dates were not changed, you can change them manually from this screen.
Monday, October 29, 2007
Prevent someone else from peeking at your Windows 2000/XP system:
If you have a Windows 2000 or Windows XP machine connected to the Internet, chances are good that your computer's security information, including user profiles, account policies, and share names are freely available to any hacker on the Internet.
This is because, by default, Windows 2000 and Windows XP do not restrict anonymous access to the above listed information.
However, you can very easily prevent others from gaining access to this sensitive information on your PC by making one very simple change to the Windows Registry.
Here's how:
1. Click on the Windows Start button.
2. Click Run.
3. Enter "Regedit" in the Run Box and click OK.
4. The Windows Registry Editor will open.
5. Drill down through the Windows Registry to get to the following key:
6. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA
7. Locate the key named restrictanonymous.
8. Double click on this key to edit it.
9. Set this key's value to 1.
10. Reboot your PC.
This setting will prevent enumeration (listing) of the Security Accounts Manager (SAM) settings on your PC. If that level of security is not strong enough for you, you can also set this key value to 2, which means that no one can access any account information on your PC without explicit anonymous permission.
This is because, by default, Windows 2000 and Windows XP do not restrict anonymous access to the above listed information.
However, you can very easily prevent others from gaining access to this sensitive information on your PC by making one very simple change to the Windows Registry.
Here's how:
1. Click on the Windows Start button.
2. Click Run.
3. Enter "Regedit" in the Run Box and click OK.
4. The Windows Registry Editor will open.
5. Drill down through the Windows Registry to get to the following key:
6. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA
7. Locate the key named restrictanonymous.
8. Double click on this key to edit it.
9. Set this key's value to 1.
10. Reboot your PC.
This setting will prevent enumeration (listing) of the Security Accounts Manager (SAM) settings on your PC. If that level of security is not strong enough for you, you can also set this key value to 2, which means that no one can access any account information on your PC without explicit anonymous permission.
Work Breakdown Structure:
A Work Breakdown Structure (WBS) is a fundamental project management technique for defining and organizing the total scope of a project, using a hierarchical tree structure. A well-designed WBS describes planned outcomes instead of planned actions. Outcomes are the desired ends of the project, and can be predicted accurately; actions comprise the project plan and may be difficult to predict accurately.
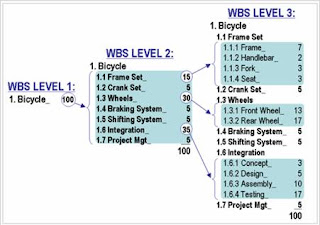
One of the most important WBS design principles is called the 100% Rule. The 100% Rule...states that the WBS includes 100% of the work defined by the project scope and captures all deliverables – internal, external, and interim – in terms of the work to be completed, including project management. The rule applies at all levels within the hierarchy: the sum of the work at the “child” level must equal 100% of the work represented by the “parent” and the WBS should not include any work that falls outside the actual scope of the project, that is, it cannot include more than 100% of the work… It is important to remember that the 100% rule also applies to the activity level. The work represented by the activities in each work package must add up to 100% of the work necessary to complete the work package.
Figure 1 shows a WBS construction technique that demonstrates the 100% Rule quantitatively. At the beginning of the design process, the project manager has assigned 100 points to the total scope of this project, which is designing and building a custom bicycle. At WBS Level 2, the 100 total points are subdivided into seven comprehensive elements. The number of points allocated to each is a judgment based on the relative effort involved; it is NOT an estimate of duration. The three largest elements of WBS Level 2 are further subdivided at Level 3, and so forth. The largest terminal elements at Level 3 represent only 17% of the total scope of work. These larger elements may be further subdivided using the progressive elaboration technique described above.
A WBS is not a project plan or a project schedule and it is not a chronological listing. It is considered poor practice to construct a project schedule (e.g. using project management software) before designing a proper WBS.
Thursday, October 25, 2007
ASKQST in iSeries:
The Ask Questions (ASKQST) command shows the Search for Answers display. From this display you can search for an answer to a question. You must first search the database to determine if an answer exists before a question can be asked.
The database used by this ASKQST command is (QSTDB):
Q/A database (QSTDB) -> Specifies the Question and Answer database in which to ask a question. Generally we are not authorized for QSTB database. In such case, the possible value to provide is: *select
Lib containing Q/A Database: *QSTLIB
If *SELECT is specified on the QSTDB parameter, any Q & A database in the
Library to which you are authorized can be selected. Generally the library used is *QSTLIB
To try the usage of this command in our AS/400 system ->
From command prompt
Type command: ASKQST + F4
1) Specify Q/A database -> *SELECT
2) Specify Lib containing Q/A database -> *QSTLIB
3) Hit enter
3) In 'Search for Answers screen' Specify the database name -> HAWKQST (All Possible questions & answers related to Hawkeye tool are been posted under this database.)
4) Specify Primary topic as *ALL (default value) or take F4 & select your choice accordingly.
5) Hit enter
6) We could find the total number of questions & answers posted in database HAWKQST from TOTAL Found Parameter in the screen.
7) Hit an enter; we would be taken to the ‘Display of Answers to Questions screen’ where in we could be able to view the questions posted & its corresponding answers. Take opt 5 against to view for the answers in detail.
Just explore what ever ASKQST Database available in our system & try to start using it if we have queries!!!!!And retrieve answers for the same..
Note: More information is also available in the Basic System Operation information in the iSeries information Center at http://www.ibm.com/eserver/iseries/infocenter.
The database used by this ASKQST command is (QSTDB):
Q/A database (QSTDB) -> Specifies the Question and Answer database in which to ask a question. Generally we are not authorized for QSTB database. In such case, the possible value to provide is: *select
Lib containing Q/A Database: *QSTLIB
If *SELECT is specified on the QSTDB parameter, any Q & A database in the
Library to which you are authorized can be selected. Generally the library used is *QSTLIB
To try the usage of this command in our AS/400 system ->
From command prompt
Type command: ASKQST + F4
1) Specify Q/A database -> *SELECT
2) Specify Lib containing Q/A database -> *QSTLIB
3) Hit enter
3) In 'Search for Answers screen' Specify the database name -> HAWKQST (All Possible questions & answers related to Hawkeye tool are been posted under this database.)
4) Specify Primary topic as *ALL (default value) or take F4 & select your choice accordingly.
5) Hit enter
6) We could find the total number of questions & answers posted in database HAWKQST from TOTAL Found Parameter in the screen.
7) Hit an enter; we would be taken to the ‘Display of Answers to Questions screen’ where in we could be able to view the questions posted & its corresponding answers. Take opt 5 against to view for the answers in detail.
Just explore what ever ASKQST Database available in our system & try to start using it if we have queries!!!!!And retrieve answers for the same..
Note: More information is also available in the Basic System Operation information in the iSeries information Center at http://www.ibm.com/eserver/iseries/infocenter.
Project Management Triangle:

Like any human undertaking, projects need to be performed and delivered under certain constraints. Traditionally, these constraints have been listed as scope, time, and cost. These are also referred to as the Project Management Triangle, where each side represents a constraint. One side of the triangle cannot be changed without impacting the others. A further refinement of the constraints separates product 'quality' or 'performance' from scope, and turns quality into a fourth constraint.
The time constraint refers to the amount of time available to complete a project. The cost constraint refers to the budgeted amount available for the project. The scope constraint refers to what must be done to produce the project's end result. These three constraints are often competing constraints: increased scope typically means increased time and increased cost, a tight time constraint could mean increased costs and reduced scope, and a tight budget could mean increased time and reduced scope.
The discipline of project management is about providing the tools and techniques that enable the project team (not just the project manager) to organize their work to meet these constraints.
Time
For analytical purposes, the time required to produce a deliverable is estimated using several techniques. One method is to identify tasks needed to produce the deliverables documented in a work breakdown structure or WBS. The work effort for each task is estimated and those estimates are rolled up into the final deliverable estimate.
The tasks are also prioritized, dependencies between tasks are identified, and this information is documented in a project schedule. The dependencies between the tasks can affect the length of the overall project (dependency constrained), as can the availability of resources (resource constrained).
Cost
Cost to develop a project depends on several variables including (chiefly): labor rates, material rates, risk management, plant (buildings, machines, etc.), equipment, and profit. When hiring an independent consultant for a project, cost will typically be determined by the consultant's or firm's per diem rate multiplied by an estimated quantity for completion.
Scope
Requirements specified for the end result. The overall definition of what the project is supposed to accomplish, and a specific description of what the end result should be or accomplish. A major component of scope is the quality of the final product. The amount of time put into individual tasks determines the overall quality of the project.
Together, these three constraints have given rise to the phrase "On Time, On Spec, On Budget".
Tuesday, October 23, 2007
Insert All:
A powerful statement that allows inserting into multiple tables at once by performing a select from the table of all the columns needed, and inserting each column's values into whichever of the target tables that is specified.
The basic syntax is something like
INSERT ALL
INTO table1 VALUES(val_A, val_B)
INTO table2 VALUES(val_C, val_D)
SELECT tmp_a val_A, tmp_b val_B, tmp_c val_C, tmp_d val_D
FROM tmp_table WHERE ...
This will insert multiple rows (any matching the where clause of the select) into both table1 and table2.
The basic syntax is something like
INSERT ALL
INTO table1 VALUES(val_A, val_B)
INTO table2 VALUES(val_C, val_D)
SELECT tmp_a val_A, tmp_b val_B, tmp_c val_C, tmp_d val_D
FROM tmp_table WHERE ...
This will insert multiple rows (any matching the where clause of the select) into both table1 and table2.
Subscribe to:
Posts (Atom)