Software documentation or source code documentation is written text that accompanies computer software. It either explains how it operates or how to use it, or may mean different things to people in different roles.
Documentation is an important part of software engineering. Types of documentation include:
• Architecture/Design - Overview of software. Includes, relations to an environment and construction principles to be used in design of software components.
• Technical - Documentation of code, algorithms, interfaces, and APIs.
• End User - Manuals for the end-user, system administrators and support staff.
• Marketing - Product briefs and promotional collateral.
Architecture/Design Documentation:
Architecture documentation is a special breed of design documents. In a way, architecture documents are third derivative from the code (design documents being second derivative, and code documents being first). These documents do not describe how to program a particular routine, or even why that particular routine exists in the form that it does, but instead merely lays out the general requirements that would motivate the existence of such a routine.
Technical Documentation:
This is what most programmers mean when using the term software documentation. When creating software, code alone is insufficient. There must be some text along with it to describe various aspects of its intended operation. It is important for the code documents to be thorough, but not so verbose that it becomes difficult to maintain them.
End User Documentation:
Typically, the user documentation describes each feature of the program, and assists the user in realizing these features. A good user document can also go so far as to provide thorough troubleshooting assistance. It is very important for user documents to not be confusing, and for them to be up to date.
Marketing Documentation:
For many applications it is necessary to have some promotional materials to encourage casual observers to spend more time learning about the product. One good marketing technique is to provide clear and memorable catch phrases that exemplify the point we wish to convey, and also emphasize the interoperability of the program with anything else provided by the manufacturer.
Wednesday, October 31, 2007
Tuesday, October 30, 2007
Updating System i5 for Daylight Saving time changes:
In the Energy Policy Act of 2005, Congress changed Daylight Saving Time (DST) in the United States so that starting this year (2007) DST begins three weeks earlier than it did last year, on the second Sunday of March. Conversely, 2007 will also see Daylight Saving Time end one week later than last year, on the first Sunday in November.
There are two ways to handle this change. You can do a manual adjustment or you can apply IBM's new Daylight Saving Time PTFs for i5 systems running i5/OS V5R3 and V5R4.
• For i5/OS V5R4, order PTFs SI26040 and SI25990
• For i5/OS V5R3, order PTFs SI26039 and SI25991
The PTFs automate the changes needed to support the new DST rules. After application, all of the time zone rules on the system will be updated to the new DST starting and ending dates.
After applying the PTF upgrade, you can check to see if the fix has been applied by performing the following steps on all your upgraded partitions:
1. Double-check the Time Zone description that your partition is using by referencing the QTIMZON system value. On a 5250 green screen, you can check this value by using this Display System Value command (DSPSYSVAL).
DSPSYSVAL SYSVAL(QTIMZON)
2. Look up the Daylight Saving Time start and end date for your time zone value by using the Work with Time Zone Descriptions command (WRKTIMZON). Run this command to display all Time Zone descriptions on your system, like this:
WRKTIMZON TIMZON(*ALL)
The Work with Time Zone Descriptions screen will display all the different time zones that are defined on your system.
To find your QTIMZON time zone on the WRKTIMZON screen, page down the list until you see either the time zone listed in QTIMZON or a time zone with a greater than sign (>) in front of it (the default time zone will always be designated in this list by a '>' sign). Place a 5=Display details in front of your default time zone entry and press Enter. On the screens that follow, you will see the starting and ending DST dates for your time zone description. What you are interested in is whether or not the PTFs changed your time zone DST start and end dates correctly.
If your time zone rule could not be changed by the PTF upgrade (as explained above), then you should change it manually by entering the following Change Time Zone Description command (CHGTIMZON) and pressing the F4 key.
CHGTIMZON TIMZON(TIME_ZONE_DESCRIPTION_NAME)
Locate the DST start and end dates on the second CHGTIMZON screen (which can be accessed by pressing the F24=More key on the first screen, followed by the F9=All key). If your time zone DST dates were not changed, you can change them manually from this screen.
There are two ways to handle this change. You can do a manual adjustment or you can apply IBM's new Daylight Saving Time PTFs for i5 systems running i5/OS V5R3 and V5R4.
• For i5/OS V5R4, order PTFs SI26040 and SI25990
• For i5/OS V5R3, order PTFs SI26039 and SI25991
The PTFs automate the changes needed to support the new DST rules. After application, all of the time zone rules on the system will be updated to the new DST starting and ending dates.
After applying the PTF upgrade, you can check to see if the fix has been applied by performing the following steps on all your upgraded partitions:
1. Double-check the Time Zone description that your partition is using by referencing the QTIMZON system value. On a 5250 green screen, you can check this value by using this Display System Value command (DSPSYSVAL).
DSPSYSVAL SYSVAL(QTIMZON)
2. Look up the Daylight Saving Time start and end date for your time zone value by using the Work with Time Zone Descriptions command (WRKTIMZON). Run this command to display all Time Zone descriptions on your system, like this:
WRKTIMZON TIMZON(*ALL)
The Work with Time Zone Descriptions screen will display all the different time zones that are defined on your system.
To find your QTIMZON time zone on the WRKTIMZON screen, page down the list until you see either the time zone listed in QTIMZON or a time zone with a greater than sign (>) in front of it (the default time zone will always be designated in this list by a '>' sign). Place a 5=Display details in front of your default time zone entry and press Enter. On the screens that follow, you will see the starting and ending DST dates for your time zone description. What you are interested in is whether or not the PTFs changed your time zone DST start and end dates correctly.
If your time zone rule could not be changed by the PTF upgrade (as explained above), then you should change it manually by entering the following Change Time Zone Description command (CHGTIMZON) and pressing the F4 key.
CHGTIMZON TIMZON(TIME_ZONE_DESCRIPTION_NAME)
Locate the DST start and end dates on the second CHGTIMZON screen (which can be accessed by pressing the F24=More key on the first screen, followed by the F9=All key). If your time zone DST dates were not changed, you can change them manually from this screen.
Monday, October 29, 2007
Prevent someone else from peeking at your Windows 2000/XP system:
If you have a Windows 2000 or Windows XP machine connected to the Internet, chances are good that your computer's security information, including user profiles, account policies, and share names are freely available to any hacker on the Internet.
This is because, by default, Windows 2000 and Windows XP do not restrict anonymous access to the above listed information.
However, you can very easily prevent others from gaining access to this sensitive information on your PC by making one very simple change to the Windows Registry.
Here's how:
1. Click on the Windows Start button.
2. Click Run.
3. Enter "Regedit" in the Run Box and click OK.
4. The Windows Registry Editor will open.
5. Drill down through the Windows Registry to get to the following key:
6. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA
7. Locate the key named restrictanonymous.
8. Double click on this key to edit it.
9. Set this key's value to 1.
10. Reboot your PC.
This setting will prevent enumeration (listing) of the Security Accounts Manager (SAM) settings on your PC. If that level of security is not strong enough for you, you can also set this key value to 2, which means that no one can access any account information on your PC without explicit anonymous permission.
This is because, by default, Windows 2000 and Windows XP do not restrict anonymous access to the above listed information.
However, you can very easily prevent others from gaining access to this sensitive information on your PC by making one very simple change to the Windows Registry.
Here's how:
1. Click on the Windows Start button.
2. Click Run.
3. Enter "Regedit" in the Run Box and click OK.
4. The Windows Registry Editor will open.
5. Drill down through the Windows Registry to get to the following key:
6. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA
7. Locate the key named restrictanonymous.
8. Double click on this key to edit it.
9. Set this key's value to 1.
10. Reboot your PC.
This setting will prevent enumeration (listing) of the Security Accounts Manager (SAM) settings on your PC. If that level of security is not strong enough for you, you can also set this key value to 2, which means that no one can access any account information on your PC without explicit anonymous permission.
Work Breakdown Structure:
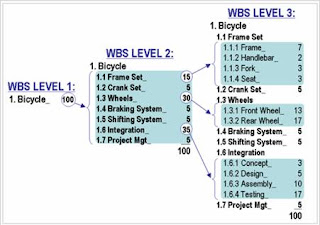
A Work Breakdown Structure (WBS) is a fundamental project management technique for defining and organizing the total scope of a project, using a hierarchical tree structure. A well-designed WBS describes planned outcomes instead of planned actions. Outcomes are the desired ends of the project, and can be predicted accurately; actions comprise the project plan and may be difficult to predict accurately.
One of the most important WBS design principles is called the 100% Rule. The 100% Rule...states that the WBS includes 100% of the work defined by the project scope and captures all deliverables – internal, external, and interim – in terms of the work to be completed, including project management. The rule applies at all levels within the hierarchy: the sum of the work at the “child” level must equal 100% of the work represented by the “parent” and the WBS should not include any work that falls outside the actual scope of the project, that is, it cannot include more than 100% of the work… It is important to remember that the 100% rule also applies to the activity level. The work represented by the activities in each work package must add up to 100% of the work necessary to complete the work package.
Figure 1 shows a WBS construction technique that demonstrates the 100% Rule quantitatively. At the beginning of the design process, the project manager has assigned 100 points to the total scope of this project, which is designing and building a custom bicycle. At WBS Level 2, the 100 total points are subdivided into seven comprehensive elements. The number of points allocated to each is a judgment based on the relative effort involved; it is NOT an estimate of duration. The three largest elements of WBS Level 2 are further subdivided at Level 3, and so forth. The largest terminal elements at Level 3 represent only 17% of the total scope of work. These larger elements may be further subdivided using the progressive elaboration technique described above.
A WBS is not a project plan or a project schedule and it is not a chronological listing. It is considered poor practice to construct a project schedule (e.g. using project management software) before designing a proper WBS.
Thursday, October 25, 2007
ASKQST in iSeries:
The Ask Questions (ASKQST) command shows the Search for Answers display. From this display you can search for an answer to a question. You must first search the database to determine if an answer exists before a question can be asked.
The database used by this ASKQST command is (QSTDB):
Q/A database (QSTDB) -> Specifies the Question and Answer database in which to ask a question. Generally we are not authorized for QSTB database. In such case, the possible value to provide is: *select
Lib containing Q/A Database: *QSTLIB
If *SELECT is specified on the QSTDB parameter, any Q & A database in the
Library to which you are authorized can be selected. Generally the library used is *QSTLIB
To try the usage of this command in our AS/400 system ->
From command prompt
Type command: ASKQST + F4
1) Specify Q/A database -> *SELECT
2) Specify Lib containing Q/A database -> *QSTLIB
3) Hit enter
3) In 'Search for Answers screen' Specify the database name -> HAWKQST (All Possible questions & answers related to Hawkeye tool are been posted under this database.)
4) Specify Primary topic as *ALL (default value) or take F4 & select your choice accordingly.
5) Hit enter
6) We could find the total number of questions & answers posted in database HAWKQST from TOTAL Found Parameter in the screen.
7) Hit an enter; we would be taken to the ‘Display of Answers to Questions screen’ where in we could be able to view the questions posted & its corresponding answers. Take opt 5 against to view for the answers in detail.
Just explore what ever ASKQST Database available in our system & try to start using it if we have queries!!!!!And retrieve answers for the same..
Note: More information is also available in the Basic System Operation information in the iSeries information Center at http://www.ibm.com/eserver/iseries/infocenter.
The database used by this ASKQST command is (QSTDB):
Q/A database (QSTDB) -> Specifies the Question and Answer database in which to ask a question. Generally we are not authorized for QSTB database. In such case, the possible value to provide is: *select
Lib containing Q/A Database: *QSTLIB
If *SELECT is specified on the QSTDB parameter, any Q & A database in the
Library to which you are authorized can be selected. Generally the library used is *QSTLIB
To try the usage of this command in our AS/400 system ->
From command prompt
Type command: ASKQST + F4
1) Specify Q/A database -> *SELECT
2) Specify Lib containing Q/A database -> *QSTLIB
3) Hit enter
3) In 'Search for Answers screen' Specify the database name -> HAWKQST (All Possible questions & answers related to Hawkeye tool are been posted under this database.)
4) Specify Primary topic as *ALL (default value) or take F4 & select your choice accordingly.
5) Hit enter
6) We could find the total number of questions & answers posted in database HAWKQST from TOTAL Found Parameter in the screen.
7) Hit an enter; we would be taken to the ‘Display of Answers to Questions screen’ where in we could be able to view the questions posted & its corresponding answers. Take opt 5 against to view for the answers in detail.
Just explore what ever ASKQST Database available in our system & try to start using it if we have queries!!!!!And retrieve answers for the same..
Note: More information is also available in the Basic System Operation information in the iSeries information Center at http://www.ibm.com/eserver/iseries/infocenter.
Project Management Triangle:

Like any human undertaking, projects need to be performed and delivered under certain constraints. Traditionally, these constraints have been listed as scope, time, and cost. These are also referred to as the Project Management Triangle, where each side represents a constraint. One side of the triangle cannot be changed without impacting the others. A further refinement of the constraints separates product 'quality' or 'performance' from scope, and turns quality into a fourth constraint.
The time constraint refers to the amount of time available to complete a project. The cost constraint refers to the budgeted amount available for the project. The scope constraint refers to what must be done to produce the project's end result. These three constraints are often competing constraints: increased scope typically means increased time and increased cost, a tight time constraint could mean increased costs and reduced scope, and a tight budget could mean increased time and reduced scope.
The discipline of project management is about providing the tools and techniques that enable the project team (not just the project manager) to organize their work to meet these constraints.
Time
For analytical purposes, the time required to produce a deliverable is estimated using several techniques. One method is to identify tasks needed to produce the deliverables documented in a work breakdown structure or WBS. The work effort for each task is estimated and those estimates are rolled up into the final deliverable estimate.
The tasks are also prioritized, dependencies between tasks are identified, and this information is documented in a project schedule. The dependencies between the tasks can affect the length of the overall project (dependency constrained), as can the availability of resources (resource constrained).
Cost
Cost to develop a project depends on several variables including (chiefly): labor rates, material rates, risk management, plant (buildings, machines, etc.), equipment, and profit. When hiring an independent consultant for a project, cost will typically be determined by the consultant's or firm's per diem rate multiplied by an estimated quantity for completion.
Scope
Requirements specified for the end result. The overall definition of what the project is supposed to accomplish, and a specific description of what the end result should be or accomplish. A major component of scope is the quality of the final product. The amount of time put into individual tasks determines the overall quality of the project.
Together, these three constraints have given rise to the phrase "On Time, On Spec, On Budget".
Tuesday, October 23, 2007
Insert All:
A powerful statement that allows inserting into multiple tables at once by performing a select from the table of all the columns needed, and inserting each column's values into whichever of the target tables that is specified.
The basic syntax is something like
INSERT ALL
INTO table1 VALUES(val_A, val_B)
INTO table2 VALUES(val_C, val_D)
SELECT tmp_a val_A, tmp_b val_B, tmp_c val_C, tmp_d val_D
FROM tmp_table WHERE ...
This will insert multiple rows (any matching the where clause of the select) into both table1 and table2.
The basic syntax is something like
INSERT ALL
INTO table1 VALUES(val_A, val_B)
INTO table2 VALUES(val_C, val_D)
SELECT tmp_a val_A, tmp_b val_B, tmp_c val_C, tmp_d val_D
FROM tmp_table WHERE ...
This will insert multiple rows (any matching the where clause of the select) into both table1 and table2.
Monday, October 22, 2007
Hot Spots:
A hotspot is an area of the session window on which you can click the left mouse button to execute a command or function. Five types of hotspots are available. They are,
1. PFnn, FPnn, Fnn, and nn Hotspots
2. Point-and-Select (Execute macro) Hotspots
3. Point-and-Select (Enter selected string) Hotspots
4. Point-and-Select (Enter at cursor position) Hotspots
5. Point-and-Select (Connect to Web Site using URL) Hotspots
The Function Key and URL hotspots are active by default, but you must activate the others before you can use them.
You must use a mouse for hotspots - they really provide a way of performing functions with a mouse rather than with keys. To use normal Hotspots, you must double-click.
Hotspots can be used to -
• Simulate function keys
• Execute a macro that has the same name as the word that you select on the screen
• Execute the word that you select
• Simulate the Enter key at the current cursor location
• Connect to a Web site by clicking on a URL that appears on the screen.
Setting Up or Changing Hotspots
1. Choose Assist from the WorkStation window menu-bar.
> The Assist pull-down menu appears.
2. Choose Hotspots Setup... from the pull-down list.
> The Select Active Hotspots dialog-box appears.
3. Choose one or more of the different types of hotspot. If you want to have 3-D Hotspots, check the appropriate Show Hotspots box too.
4. Push the OK button.
> The dialog-box disappears and the hotspots you chose are activated.
1. PFnn, FPnn, Fnn, and nn Hotspots
2. Point-and-Select (Execute macro) Hotspots
3. Point-and-Select (Enter selected string) Hotspots
4. Point-and-Select (Enter at cursor position) Hotspots
5. Point-and-Select (Connect to Web Site using URL) Hotspots
The Function Key and URL hotspots are active by default, but you must activate the others before you can use them.
You must use a mouse for hotspots - they really provide a way of performing functions with a mouse rather than with keys. To use normal Hotspots, you must double-click.
Hotspots can be used to -
• Simulate function keys
• Execute a macro that has the same name as the word that you select on the screen
• Execute the word that you select
• Simulate the Enter key at the current cursor location
• Connect to a Web site by clicking on a URL that appears on the screen.
Setting Up or Changing Hotspots
1. Choose Assist from the WorkStation window menu-bar.
> The Assist pull-down menu appears.
2. Choose Hotspots Setup... from the pull-down list.
> The Select Active Hotspots dialog-box appears.
3. Choose one or more of the different types of hotspot. If you want to have 3-D Hotspots, check the appropriate Show Hotspots box too.
4. Push the OK button.
> The dialog-box disappears and the hotspots you chose are activated.
Sunday, October 21, 2007
Bricks and Clicks:
Bricks-and-clicks is a business model by which a company integrates both offline (bricks) and online (clicks) presences. It is also known as click-and-mortar or clicks-and-bricks, as well as bricks, clicks and flips, flips referring to catalogs.
For example, an electronics store may allow the user to order online, but pick up their order immediately at a local store, which the user finds using locator software. Conversely, a furniture store may have displays at a local store from which a customer can order an item electronically for delivery.
The bricks and clicks model has typically been used by traditional retailers who have extensive logistics and supply chains. Part of the reason for its success is that it is far easier for a traditional retailer to establish an online presence than it is for a start-up company to employ a successful pure "dot com" strategy, or for an online retailer to establish a traditional presence (including a strong brand).
Advantages of the Model:
Click and mortar firms have the advantage in areas of existing products and services. This is because they are able to use their competencies and assets, which include:
1. Core competency. Successful firms tend to have one or two core competencies that they can do better than their competitors. It may be anything from new product development to customer service. When a bricks and mortar firm goes online it is able to use this core competency more intensively and extensively.
2. Existing supplier networks. Existing firms have established relationships of trust with suppliers. This usually ensures problem free delivery and an assured supply. It can also entail price discounts and other preferential treatment.
3. Existing distribution channels. As with supplier networks, existing distribution channels can ensure problem free delivery, price discounts, and preferential treatments.
4. Brand equity. Often existing firms have invested large sums of money in brand advertising over the years.
5. Stability. Existing firms that have been in business for many years appear more stable. People trust them more than pure on-line firms. This is particularly true in financial services.
6. Existing customer base. Because existing firms already have a base of sales, they can more easily obtain economies of scale in promotion, purchasing and production; economies of scope in distribution and promotion; reduced overhead allocation per unit; and shorter break even times.
7. A lower cost of capital. Established firms will have a lower cost of capital. Bond issues may be available to existing firms that are not available to dot coms. The underwriting cost of a dot com IPO is higher than an equivalent brick and click equity offering.
8. Learning curve advantages. Every industry has a set of best practices that are more or less known to established firms. New dot coms will be at a disadvantage unless they can redefine the industry's best practices and leap frog existing firms.
Pure dot coms, on the other hand, have the advantage in areas of new e-business models that stress cost efficiency. They are not burdened with brick and mortar costs and can offer products at very low marginal cost. However, they do tend to spend substantially more on customer acquisition.
For example, an electronics store may allow the user to order online, but pick up their order immediately at a local store, which the user finds using locator software. Conversely, a furniture store may have displays at a local store from which a customer can order an item electronically for delivery.
The bricks and clicks model has typically been used by traditional retailers who have extensive logistics and supply chains. Part of the reason for its success is that it is far easier for a traditional retailer to establish an online presence than it is for a start-up company to employ a successful pure "dot com" strategy, or for an online retailer to establish a traditional presence (including a strong brand).
Advantages of the Model:
Click and mortar firms have the advantage in areas of existing products and services. This is because they are able to use their competencies and assets, which include:
1. Core competency. Successful firms tend to have one or two core competencies that they can do better than their competitors. It may be anything from new product development to customer service. When a bricks and mortar firm goes online it is able to use this core competency more intensively and extensively.
2. Existing supplier networks. Existing firms have established relationships of trust with suppliers. This usually ensures problem free delivery and an assured supply. It can also entail price discounts and other preferential treatment.
3. Existing distribution channels. As with supplier networks, existing distribution channels can ensure problem free delivery, price discounts, and preferential treatments.
4. Brand equity. Often existing firms have invested large sums of money in brand advertising over the years.
5. Stability. Existing firms that have been in business for many years appear more stable. People trust them more than pure on-line firms. This is particularly true in financial services.
6. Existing customer base. Because existing firms already have a base of sales, they can more easily obtain economies of scale in promotion, purchasing and production; economies of scope in distribution and promotion; reduced overhead allocation per unit; and shorter break even times.
7. A lower cost of capital. Established firms will have a lower cost of capital. Bond issues may be available to existing firms that are not available to dot coms. The underwriting cost of a dot com IPO is higher than an equivalent brick and click equity offering.
8. Learning curve advantages. Every industry has a set of best practices that are more or less known to established firms. New dot coms will be at a disadvantage unless they can redefine the industry's best practices and leap frog existing firms.
Pure dot coms, on the other hand, have the advantage in areas of new e-business models that stress cost efficiency. They are not burdened with brick and mortar costs and can offer products at very low marginal cost. However, they do tend to spend substantially more on customer acquisition.
Thursday, October 18, 2007
Run CL Commands from Interactive SQL Sessions:
When we are in the interactive SQL Session and if we need to run a CL command in it then type ‘CALL QCMD’ in the space available for SQL statements. This will bring up the command entry screen where the CL commands can be executed.
Wednesday, October 17, 2007
Payroll & Garnishment:
In a company, payroll is the sum of all financial records of salaries, wages, bonuses, and deductions.
A pay stub, paystub, pay slip, pay advice, or sometimes paycheck stub, is a document that an employee receives either as a notice that the direct deposit transaction has gone through, or as part of their paycheck. It will typically detail the gross income and all taxes and any other deductions such as retirement plan contributions, insurances, garnishments, or charitable contributions taken out of the gross amount to arrive at the final net amount of the pay, also including the year to date totals in some circumstances.
A garnishment is a means of collecting a monetary judgment against a defendant by ordering a third party (the garnishee) to pay money, otherwise owed to the defendant, directly to the plaintiff.
Wage garnishment, the most common type of garnishment, is the process of deducting money from an employee's monetary compensation (including salary) as a result of a court order. In the United States, such payments are limited by federal law to 25 percent of the disposable income that the employee earns. Garnishments can be taken for any type of debt but common examples of debt that result in garnishments include:
• child support
• taxes
• Unpaid Court Fines
• any other type of money judgment
When served on an employer, garnishments are taken as part of the payroll process. When processing payroll, sometimes there is not enough money in the employee's net pay to satisfy all of the garnishments. In such a case, the correct order to take a garnishment must be satisfied. For example, in a case with federal tax, local tax, and credit card garnishments, the first garnishment taken would be the federal tax garnishments, then the local tax garnishments, and finally, garnishments for the credit card.
The other type of garnishment, also known as attachment, (or attachment of earnings), requires the garnishee to deliver all the defendant's money and/or property in the hands of the garnishee at the time of service of process to the court, to be paid over to the plaintiff. Since this type of garnishment is not continuing in nature, but is not subject to the type of restrictions that apply to wage garnishment, it is most often used against banks, or other persons or companies that incur liquidated obligations in the regular course of business.
A pay stub, paystub, pay slip, pay advice, or sometimes paycheck stub, is a document that an employee receives either as a notice that the direct deposit transaction has gone through, or as part of their paycheck. It will typically detail the gross income and all taxes and any other deductions such as retirement plan contributions, insurances, garnishments, or charitable contributions taken out of the gross amount to arrive at the final net amount of the pay, also including the year to date totals in some circumstances.
A garnishment is a means of collecting a monetary judgment against a defendant by ordering a third party (the garnishee) to pay money, otherwise owed to the defendant, directly to the plaintiff.
Wage garnishment, the most common type of garnishment, is the process of deducting money from an employee's monetary compensation (including salary) as a result of a court order. In the United States, such payments are limited by federal law to 25 percent of the disposable income that the employee earns. Garnishments can be taken for any type of debt but common examples of debt that result in garnishments include:
• child support
• taxes
• Unpaid Court Fines
• any other type of money judgment
When served on an employer, garnishments are taken as part of the payroll process. When processing payroll, sometimes there is not enough money in the employee's net pay to satisfy all of the garnishments. In such a case, the correct order to take a garnishment must be satisfied. For example, in a case with federal tax, local tax, and credit card garnishments, the first garnishment taken would be the federal tax garnishments, then the local tax garnishments, and finally, garnishments for the credit card.
The other type of garnishment, also known as attachment, (or attachment of earnings), requires the garnishee to deliver all the defendant's money and/or property in the hands of the garnishee at the time of service of process to the court, to be paid over to the plaintiff. Since this type of garnishment is not continuing in nature, but is not subject to the type of restrictions that apply to wage garnishment, it is most often used against banks, or other persons or companies that incur liquidated obligations in the regular course of business.
Display Two Subfiles at once:
There are two ways to display two subfiles at once--one above the other or side by side. OS/400 directly supports the first method. The trick is in the way we read and write to the subfiles in the RPG program.
Here's the DDS for display file SFLDEMO1, which has two subfiles:
A DSPSIZ(24 80 *DS3)
A CA03 CA12
A
A R SFL1 SFL
A DATA1 20 2 2
A
A R CTL1 SFLCTL(SFL1)
A SFLDSP
A SFLDSPCTL
A N01 SFLEND(*MORE)
A SFLSIZ(9)
A SFLPAG(8)
A 1 5'SFL 1'
A RRN1 4S 0H
A
A R SFL2 SFL
A DATA2 20 12 2
A
A R CTL2 SFLCTL(SFL2)
A SFLDSP
A SFLDSPCTL
A N01 SFLEND(*MORE)
A SFLSIZ(9)
A SFLPAG(8)
A OVERLAY
A 11 5'SFL 2'
A RRN2 4S 0H
Here's the RPG program that drives it:
Fsfldemo1d cf e workstn sfile(sfl1: rrn1)
F sfile(sfl2: rrn2)
/free
for rrn1 = 1 to 27;
data1 = '1:' + %char(rrn1);
write sfl1;
endfor;
for rrn2 = 1 to 34;
data2 = '2:' + %char(rrn2);
write sfl2;
endfor;
write ctl1;
exfmt ctl2;
read ctl1;
*inlr = *on;
Notice the I/O operations. First write to the first subfile control format, use the EXFMT op code to write and read the second control format, and, finally, read the first control format. It works every time. Which subfile rolls, depends on where the cursor is located. To roll a certain subfile, place the cursor on the subfile or on its control record.
Side by side subfile has to be handled by programming as OS/400 will not handle it automatically.
Here's the DDS for display file SFLDEMO1, which has two subfiles:
A DSPSIZ(24 80 *DS3)
A CA03 CA12
A
A R SFL1 SFL
A DATA1 20 2 2
A
A R CTL1 SFLCTL(SFL1)
A SFLDSP
A SFLDSPCTL
A N01 SFLEND(*MORE)
A SFLSIZ(9)
A SFLPAG(8)
A 1 5'SFL 1'
A RRN1 4S 0H
A
A R SFL2 SFL
A DATA2 20 12 2
A
A R CTL2 SFLCTL(SFL2)
A SFLDSP
A SFLDSPCTL
A N01 SFLEND(*MORE)
A SFLSIZ(9)
A SFLPAG(8)
A OVERLAY
A 11 5'SFL 2'
A RRN2 4S 0H
Here's the RPG program that drives it:
Fsfldemo1d cf e workstn sfile(sfl1: rrn1)
F sfile(sfl2: rrn2)
/free
for rrn1 = 1 to 27;
data1 = '1:' + %char(rrn1);
write sfl1;
endfor;
for rrn2 = 1 to 34;
data2 = '2:' + %char(rrn2);
write sfl2;
endfor;
write ctl1;
exfmt ctl2;
read ctl1;
*inlr = *on;
Notice the I/O operations. First write to the first subfile control format, use the EXFMT op code to write and read the second control format, and, finally, read the first control format. It works every time. Which subfile rolls, depends on where the cursor is located. To roll a certain subfile, place the cursor on the subfile or on its control record.
Side by side subfile has to be handled by programming as OS/400 will not handle it automatically.
Monday, October 15, 2007
Control Charts:
Control charts provide a way of objectively defining a process and variation. The intent of a control chart is to determine if a process is statistically stable and then to monitor the variation of stable process where activities are repetitive.
There are two types of variation:
1. Common or random causes of variation
These are inherent in every system over time, and are a part of the natural operation of the system. Resolving common cause problems requires a process change.
2. Special causes of variation
These are not part of the system all the time. They result from some special circumstance and require changes outside the process for resolution.
Common causes of variation are typically due to many small random sources of variation. The sum of these sources of variation determines the magnitude of the processes inherent variation due to common causes. From the sum, the process control limits and current process capability can be determined. Accepted practice uses a width of three standard deviations around the population mean (μ ± 3δ) to establish the control limits.
A process containing only common causes of variation is considered stable, which implies that the variation is predictable within the statistically established control limits. Processes containing special as well as common causes of variation are referred to as unstable processes.
Control charts are suitable for tracking items such as:
• Production failures
• Defects by life cycle phase
• Complaint/failures by application/software
• Response time to change request
• Cycle times/delivery times
• Mean time to failure
There are two types of variation:
1. Common or random causes of variation
These are inherent in every system over time, and are a part of the natural operation of the system. Resolving common cause problems requires a process change.
2. Special causes of variation
These are not part of the system all the time. They result from some special circumstance and require changes outside the process for resolution.
Common causes of variation are typically due to many small random sources of variation. The sum of these sources of variation determines the magnitude of the processes inherent variation due to common causes. From the sum, the process control limits and current process capability can be determined. Accepted practice uses a width of three standard deviations around the population mean (μ ± 3δ) to establish the control limits.
A process containing only common causes of variation is considered stable, which implies that the variation is predictable within the statistically established control limits. Processes containing special as well as common causes of variation are referred to as unstable processes.
Control charts are suitable for tracking items such as:
• Production failures
• Defects by life cycle phase
• Complaint/failures by application/software
• Response time to change request
• Cycle times/delivery times
• Mean time to failure
FTP to Printer file:
Sometimes we use to FTP a file from a PC to our iSeries, and then run a batch job to print it out. There is a way to eliminate the batch job. Here's how it works.
First, create a program-described printer file.
crtprtf mylib/myprtf outq(myoutq) . . .
Second, use the put subcommand in an FTP client to write to the printer file. The following command prints file data.txt, which is in the temp directory of the client machine, on the iSeries.
put /temp/data.txt mylib/myprtf
First, create a program-described printer file.
crtprtf mylib/myprtf outq(myoutq) . . .
Second, use the put subcommand in an FTP client to write to the printer file. The following command prints file data.txt, which is in the temp directory of the client machine, on the iSeries.
put /temp/data.txt mylib/myprtf
Thursday, October 11, 2007
Logistics Management:
Logistics is the art and science of managing and controlling the flow of goods, energy, information and other resources like products, services and people from the source of production to the marketplace. It involves the integration of information, transportation, inventory, warehousing, material handling, and packaging. The operating responsibility of logistics is the geographical repositioning of raw materials, work in process and finished inventories where required at the lowest cost possible.
Logistics management is that part of the supply chain which plans, implements and controls the efficient, effective forward and reverse flow and storage of goods, services and related information between the point of origin and the point of consumption in order to meet customers' requirements. A professional working in the field of logistics management is called a logistician.
Logistics automation is the application of computer software and / or automated machinery to improve the efficiency of logistics operations. Typically this refers to operations within a warehouse or distribution center, with broader tasks undertaken by supply chain management systems and enterprise resource planning systems.
Logistics automation systems can powerfully complement the facilities provided by these higher level computer systems. The focus on an individual node within a wider logistics network allows systems to be highly tailored to the requirements of that node.
A logistics automation system may provide the following:
• Automated goods in processes: Incoming goods can be marked with barcodes and the automation system notified of the expected stock. On arrival, the goods can be scanned and thereby identified, and taken via conveyors, sortation systems, and automated cranes into an automatically assigned storage location.
• Automated Goods Retrieval for Orders: On receipt of orders, the automation system is able to immediately locate goods and retrieve them to a pickface location.
• Automated dispatch processing: Combining knowledge of all orders placed at the warehouse the automation system can assign picked goods into dispatch units and then into outbound loads. Sortation systems and conveyors can then move these onto the outgoing trailers.
A complete warehouse automation system can drastically reduce the workforce required to run a facility, with human input required only for a few tasks, such as picking units of product from a bulk packed case
Logistics management is that part of the supply chain which plans, implements and controls the efficient, effective forward and reverse flow and storage of goods, services and related information between the point of origin and the point of consumption in order to meet customers' requirements. A professional working in the field of logistics management is called a logistician.
Logistics automation is the application of computer software and / or automated machinery to improve the efficiency of logistics operations. Typically this refers to operations within a warehouse or distribution center, with broader tasks undertaken by supply chain management systems and enterprise resource planning systems.
Logistics automation systems can powerfully complement the facilities provided by these higher level computer systems. The focus on an individual node within a wider logistics network allows systems to be highly tailored to the requirements of that node.
A logistics automation system may provide the following:
• Automated goods in processes: Incoming goods can be marked with barcodes and the automation system notified of the expected stock. On arrival, the goods can be scanned and thereby identified, and taken via conveyors, sortation systems, and automated cranes into an automatically assigned storage location.
• Automated Goods Retrieval for Orders: On receipt of orders, the automation system is able to immediately locate goods and retrieve them to a pickface location.
• Automated dispatch processing: Combining knowledge of all orders placed at the warehouse the automation system can assign picked goods into dispatch units and then into outbound loads. Sortation systems and conveyors can then move these onto the outgoing trailers.
A complete warehouse automation system can drastically reduce the workforce required to run a facility, with human input required only for a few tasks, such as picking units of product from a bulk packed case
Wednesday, October 10, 2007
Make a CL program or Module to retrieve its Name:
The trick is to make a program send a message to itself and retrieve the program name from the message about the sender. The following code works in OPM CL programs, ILE CL programs, and ILE CL modules.
dcl &MsgKey *char 4
dcl &PgmName *char 10
dcl &Sender *char 80
sndpgmmsg msg(' ') topgmq(*same) msgtype(*info) keyvar(&msgkey)
rcvmsg pgmq(*same) msgtype(*info) sender(&sender) rmv(*yes)
chgvar &PgmName %sst(&Sender 56 10)
In the case of CL modules, you should know that this routine returns the name of the program in which this module is bound, not the name of the module. In ILE modules, the following code retrieves both program name and module name.
dcl &MsgKey *char 4
dcl &PgmName *char 10
dcl &ModName *char 10
dcl &Sender *char 720
sndpgmmsg msg(' ') topgmq(*same) msgtype(*info) keyvar(&msgkey
rcvmsg pgmq(*same) msgtype(*info) rmv(*yes) +
sender(&sender) senderfmt(*long)
chgvar &PgmName %sst(&Sender 42 10)
chgvar &ModName %sst(&Sender 54 10)
dcl &MsgKey *char 4
dcl &PgmName *char 10
dcl &Sender *char 80
sndpgmmsg msg(' ') topgmq(*same) msgtype(*info) keyvar(&msgkey)
rcvmsg pgmq(*same) msgtype(*info) sender(&sender) rmv(*yes)
chgvar &PgmName %sst(&Sender 56 10)
In the case of CL modules, you should know that this routine returns the name of the program in which this module is bound, not the name of the module. In ILE modules, the following code retrieves both program name and module name.
dcl &MsgKey *char 4
dcl &PgmName *char 10
dcl &ModName *char 10
dcl &Sender *char 720
sndpgmmsg msg(' ') topgmq(*same) msgtype(*info) keyvar(&msgkey
rcvmsg pgmq(*same) msgtype(*info) rmv(*yes) +
sender(&sender) senderfmt(*long)
chgvar &PgmName %sst(&Sender 42 10)
chgvar &ModName %sst(&Sender 54 10)
Tuesday, October 9, 2007
Quality Baseline:
Developing a baseline is performing an analysis/study to determine the current level of performance in a specific activity. For example, if one were to baseline the software development process the baseline could include quantitative data on defect rates, resources expended by phase, productivity rates such as function points per person-month, and levels or amounts of documentation.
A baseline needs to be established for two reasons: first, to identify perceived quality problems; and second, to establish a baseline from which quality improvement objectives can be established and improvements in quality quantitatively measured.
Baseline studies can be conducted in one of the following two manners:
Evaluate entire population
This means all of the parties or products involved will be surveyed. This method is normally most effective when the information to be analyzed is automated. For example, when looking at factors such as schedule and budget.
Sample survey
Using this method, only a part of the population of people/products is surveyed. This approach is normally most effective when there is a large population to be surveyed and the data is not automated. While sampling should be done statistically, it is not essential in these studies for valid statistical samples to be drawn.
The following are typical steps needed to perform a baseline study.
1. Identify products/services to be surveyed
2. Define conformance and nonconformance
3. Identify survey population
4. Identify size of population to be surveyed
5. Develop survey instrument
6. Conduct survey
7. Follow up on incomplete surveys
8. Accumulate and present survey results
9. Take action and notify participants of that action
A baseline needs to be established for two reasons: first, to identify perceived quality problems; and second, to establish a baseline from which quality improvement objectives can be established and improvements in quality quantitatively measured.
Baseline studies can be conducted in one of the following two manners:
Evaluate entire population
This means all of the parties or products involved will be surveyed. This method is normally most effective when the information to be analyzed is automated. For example, when looking at factors such as schedule and budget.
Sample survey
Using this method, only a part of the population of people/products is surveyed. This approach is normally most effective when there is a large population to be surveyed and the data is not automated. While sampling should be done statistically, it is not essential in these studies for valid statistical samples to be drawn.
The following are typical steps needed to perform a baseline study.
1. Identify products/services to be surveyed
2. Define conformance and nonconformance
3. Identify survey population
4. Identify size of population to be surveyed
5. Develop survey instrument
6. Conduct survey
7. Follow up on incomplete surveys
8. Accumulate and present survey results
9. Take action and notify participants of that action
Monday, October 8, 2007
Case Insensitive sorting in SQL/400:
In SQL, the default sort sequence is done by the Hexadecimal value of the characters. As a result of this when character sorting is performed, lower case letter are sorted first followed by the upper case characters. This results in irregular or undesirable results. Following is the solution available to avoid this problem.
In interactive SQL, press the F13 key and select option 1 ("change session defaults"). Page down once and change the sort sequence entry to *LANGIDSHR.
For programs that include embedded SQL, we have two choices. One method is to change the SRTSEQ parameter of the command that is used to create the program (for example, CRTSQLRPGI). The better solution is to code a SET OPTION command in the source code, as the following RPG snippet illustrates.
C/exec sql
C+ set option srtseq=*langidshr
C/end-exec
This set up process sorts the record based on the character in the language and not by its hex values.
In interactive SQL, press the F13 key and select option 1 ("change session defaults"). Page down once and change the sort sequence entry to *LANGIDSHR.
For programs that include embedded SQL, we have two choices. One method is to change the SRTSEQ parameter of the command that is used to create the program (for example, CRTSQLRPGI). The better solution is to code a SET OPTION command in the source code, as the following RPG snippet illustrates.
C/exec sql
C+ set option srtseq=*langidshr
C/end-exec
This set up process sorts the record based on the character in the language and not by its hex values.
Sunday, October 7, 2007
Verification versus Validation:
Verification and Validation are the two forms of testing software.
Verification ensures that the system (software, hardware, documentation, and personnel) complies with an organization’s standards and processes, relying on review of non-executable methods.
Validation physically ensures that the system operates according to plan by executing the system functions through a series of tests that can be observed and evaluated.
Verification answers the question, “Did we build the right system?” while validation addresses, “Did we build the system right?”
Verification requires several types of reviews, including requirements reviews, design reviews, code walkthroughs, code inspections, and test reviews. The system user should be involved in these reviews to find defects before they are built into the system. In the case of purchased systems, user input is needed to assure that the supplier makes the appropriate tests to eliminate defects.
Validation is accomplished simply by executing a real-life function. This includes unit testing, integration testing, system testing and user acceptance testing. In this rigorous testing is conducted to validate if the system meets the functional requirement.
Verification ensures that the system (software, hardware, documentation, and personnel) complies with an organization’s standards and processes, relying on review of non-executable methods.
Validation physically ensures that the system operates according to plan by executing the system functions through a series of tests that can be observed and evaluated.
Verification answers the question, “Did we build the right system?” while validation addresses, “Did we build the system right?”
Verification requires several types of reviews, including requirements reviews, design reviews, code walkthroughs, code inspections, and test reviews. The system user should be involved in these reviews to find defects before they are built into the system. In the case of purchased systems, user input is needed to assure that the supplier makes the appropriate tests to eliminate defects.
Validation is accomplished simply by executing a real-life function. This includes unit testing, integration testing, system testing and user acceptance testing. In this rigorous testing is conducted to validate if the system meets the functional requirement.
Friday, October 5, 2007
Save-Restore Commands:
We have a partition for production and one for development. We struggle with copying data and source code between the two machines. FTP copies source members without a problem, but it drops the modification dates on the source records. To copy data files, we can use save files in binary mode, which is a hassle. Also, setting up a scheduled job to refresh certain files on the test system from the production system at night, and while FTP would work; it would be difficult for the job to determine if the transmission succeeded.
A better way to this is to use the SAVRSTxxx commands, especially Save Restore Object (SAVRSTOBJ). Two other commands that we might need occasionally are Save Restore Library (SAVRSTLIB) and Save Restore Objects (SAVRST), for the IFS. There is also Save Restore Configuration (SAVRSTCFG), Save Restore Changed Objects (SAVRSTCHG), and Save Restore Doc/Lib Object (SAVRSTDLO) commands.
The SAVRSTxxx commands go through a process similar to the binary FTP of save files, but without the hassle. Here are some examples.
This command copies data file SOMEFILE from the production system to the DEV system.
SAVRSTOBJ OBJ(SOMEFILE) LIB(MYLIB) RMTLOCNAME(DEV)
OBJTYPE(*FILE)
This command copies an entire source physical file to the test system.
SAVRSTOBJ OBJ(QRPGLESRC) LIB(MYLIB) RMTLOCNAME(DEV)
Here's a command to copy one RPG source member, MYSRCMBR, from production to Development. Notice MBROPT(*NEW) was used here, because the source member did not already exist in QRPGLESRC on the Development system.
SAVRSTOBJ OBJ(QRPGLESRC) LIB(MYLIB) RMTLOCNAME(DEV)
OBJTYPE(*FILE) FILEMBR((QRPGLESRC (MYSRCMBR))) MBROPT(*NEW)
Another nice thing about the SAVRSTxxx commands is that they do not require enrollment in the system distribution directory, as SNDNETF (Send Network File) does.
A better way to this is to use the SAVRSTxxx commands, especially Save Restore Object (SAVRSTOBJ). Two other commands that we might need occasionally are Save Restore Library (SAVRSTLIB) and Save Restore Objects (SAVRST), for the IFS. There is also Save Restore Configuration (SAVRSTCFG), Save Restore Changed Objects (SAVRSTCHG), and Save Restore Doc/Lib Object (SAVRSTDLO) commands.
The SAVRSTxxx commands go through a process similar to the binary FTP of save files, but without the hassle. Here are some examples.
This command copies data file SOMEFILE from the production system to the DEV system.
SAVRSTOBJ OBJ(SOMEFILE) LIB(MYLIB) RMTLOCNAME(DEV)
OBJTYPE(*FILE)
This command copies an entire source physical file to the test system.
SAVRSTOBJ OBJ(QRPGLESRC) LIB(MYLIB) RMTLOCNAME(DEV)
Here's a command to copy one RPG source member, MYSRCMBR, from production to Development. Notice MBROPT(*NEW) was used here, because the source member did not already exist in QRPGLESRC on the Development system.
SAVRSTOBJ OBJ(QRPGLESRC) LIB(MYLIB) RMTLOCNAME(DEV)
OBJTYPE(*FILE) FILEMBR((QRPGLESRC (MYSRCMBR))) MBROPT(*NEW)
Another nice thing about the SAVRSTxxx commands is that they do not require enrollment in the system distribution directory, as SNDNETF (Send Network File) does.
Wednesday, October 3, 2007
Assertive Communication:
Do you have trouble saying NO, even when you really should?
Do you feel like people walk all over you?
Do you have trouble keeping your temper under control?
If you answered yes to any of the above questions, you might find it really helpful to learn about assertive communication.
I. What is Assertiveness?
Assertiveness is the ability to honestly express your opinions, feelings, attitudes, and rights, without undue anxiety, in a way that doesn't infringe on the rights of others.
It's not aggressiveness; it's a middle ground between being a bully and a doormat.
II. Why is Assertiveness Important?
If you don't know how to be assertive, you might experience Depression, Resentment, Frustration, Temper/violence, Anxiety, Poor relationships, Physical complaints and Parenting problems.
A note about selective assertiveness:
Most people find it easier to be assertive in some situations than in others. This makes perfect sense. It's a lot easier to hold your ground with a stranger than with someone you love who might get angry if you express your true feelings. But the more important the relationship is to you, the more important it is to be assertive.
III. Techniques:
How to be effectively assertive:
Use assertive body language. Face the other person, stand or sit straight, don't use dismissive gestures, be sure you have a pleasant, but serious facial expression, keep your voice calm and soft, not whiney or abrasive.
Use "I" statements. Keep the focus on the problem you're having, not on accusing or blaming the other person. Example: "I'd like to be able to tell my stories without interruption." instead of "You're always interrupting my stories!"
Use facts, not judgments. Example: "Your punctuation needs work and your formatting is inconsistent" instead of "This is sloppy work." or "Did you know that shirt has some spots?" instead of "You're not going out looking like THAT, are you?"
Express ownership of your thoughts, feeling, and opinions. Example: "I get angry when he breaks his promises." instead of "He makes me angry." or "I believe the best policy is to…" instead of "The only sensible thing is to …"
Make clear, direct, requests. Don't invite the person to say no. Example: "Will you please ... ?" instead of "Would you mind … ?" or "Why don't you … ?"
Do you feel like people walk all over you?
Do you have trouble keeping your temper under control?
If you answered yes to any of the above questions, you might find it really helpful to learn about assertive communication.
I. What is Assertiveness?
Assertiveness is the ability to honestly express your opinions, feelings, attitudes, and rights, without undue anxiety, in a way that doesn't infringe on the rights of others.
It's not aggressiveness; it's a middle ground between being a bully and a doormat.
II. Why is Assertiveness Important?
If you don't know how to be assertive, you might experience Depression, Resentment, Frustration, Temper/violence, Anxiety, Poor relationships, Physical complaints and Parenting problems.
A note about selective assertiveness:
Most people find it easier to be assertive in some situations than in others. This makes perfect sense. It's a lot easier to hold your ground with a stranger than with someone you love who might get angry if you express your true feelings. But the more important the relationship is to you, the more important it is to be assertive.
III. Techniques:
How to be effectively assertive:
Use assertive body language. Face the other person, stand or sit straight, don't use dismissive gestures, be sure you have a pleasant, but serious facial expression, keep your voice calm and soft, not whiney or abrasive.
Use "I" statements. Keep the focus on the problem you're having, not on accusing or blaming the other person. Example: "I'd like to be able to tell my stories without interruption." instead of "You're always interrupting my stories!"
Use facts, not judgments. Example: "Your punctuation needs work and your formatting is inconsistent" instead of "This is sloppy work." or "Did you know that shirt has some spots?" instead of "You're not going out looking like THAT, are you?"
Express ownership of your thoughts, feeling, and opinions. Example: "I get angry when he breaks his promises." instead of "He makes me angry." or "I believe the best policy is to…" instead of "The only sensible thing is to …"
Make clear, direct, requests. Don't invite the person to say no. Example: "Will you please ... ?" instead of "Would you mind … ?" or "Why don't you … ?"
Tuesday, October 2, 2007
Welcome the P-Field:
P-fields are one-byte codes that control the color and attributes of a field in a display file. Before P-fields were added to data description specifications (DDS), it was necessary for a programmer to make decisions about color and attributes during development. Whichever attributes were selected had to be included in the DDS. To apply different attributes to a field in different circumstances required the use of conditioning indicators.
In the following example, the NAME field is shown in blue. ADDRESS appears in white and will be underlined if indicator 11 is on. The color and attributes of the PHONE field depend on the setting of indicators 12, 13, 15, and 16.
A NAME 20A O 10 6COLOR(BLU)
A ADDRESS 20A O 11 6COLOR(WHT)
A 11 DSPATR(UL)
A PHONE 12A O 12 6
A N15N16 COLOR(BLU)
A N15 16 COLOR(RED)
A 15N16 COLOR(PNK)
A 15 16 COLOR(WHT)
A 12 DSPATR(RI)
A 13 DSPATR(UL)
It works, but it's hardly any fun.
P-fields allows to determine color and attributes at run time without using indicators. Load a P-field with a character in one of two ranges--hexadecimal 20 through 3F or hexadecimal A0 through BF--and the system takes care of the rest. These hex values and their meanings are listed under the discussion of the DSPATR keyword in the DDS reference. Notice that P-fields can't be used for attributes MDT (modified data tag), OID (operator identification), PC (position cursor), and SP (select by light pen).
In the following display file fragment, the NAME field's attributes are controlled by the value in the NAMEATTR field.
A NAME 20A B 10 6DSPATR(&NAMEATTR)
A NAMEATTR 1A P
Notice the usage entry of P for the NAMEATTR field. This tells the system that NAMEATTR is a P-field.
One way an RPG program might load a value into a P-field is by assigning a hexadecimal literal, like this:
nameattr = x'28';
The hex 28 value causes the field to blink on a dumb terminal and to be displayed in red on a not-quite-so-dumb terminal. That's not obvious enough. The source code will be more readable if we assign a named constant to the P-field, like this:
D Blink C Const(x'28')
NameAttr = Blink;
But the P-field value does not have to be hard-coded in the program's source code. It could be stored in a file or data area, passed into a program through a parameter, assigned a value according to user input, and so on.
P-fields are a superior alternative to indicators. Using P-fields with named constants that represent display attributes results in clearer code. P-fields can be stored in external objects like files and data areas or passed to a program through parameters.
However, that does not mean we should use P-fields only. Having to create a P-field for every data field on a display can get unwieldy. If a field always has a certain color or display attribute (it's always underlined, for example), it may not be worth the trouble to use a P-field. But for those times when you need more flexibility, P-fields are the way to go.
In the following example, the NAME field is shown in blue. ADDRESS appears in white and will be underlined if indicator 11 is on. The color and attributes of the PHONE field depend on the setting of indicators 12, 13, 15, and 16.
A NAME 20A O 10 6COLOR(BLU)
A ADDRESS 20A O 11 6COLOR(WHT)
A 11 DSPATR(UL)
A PHONE 12A O 12 6
A N15N16 COLOR(BLU)
A N15 16 COLOR(RED)
A 15N16 COLOR(PNK)
A 15 16 COLOR(WHT)
A 12 DSPATR(RI)
A 13 DSPATR(UL)
It works, but it's hardly any fun.
P-fields allows to determine color and attributes at run time without using indicators. Load a P-field with a character in one of two ranges--hexadecimal 20 through 3F or hexadecimal A0 through BF--and the system takes care of the rest. These hex values and their meanings are listed under the discussion of the DSPATR keyword in the DDS reference. Notice that P-fields can't be used for attributes MDT (modified data tag), OID (operator identification), PC (position cursor), and SP (select by light pen).
In the following display file fragment, the NAME field's attributes are controlled by the value in the NAMEATTR field.
A NAME 20A B 10 6DSPATR(&NAMEATTR)
A NAMEATTR 1A P
Notice the usage entry of P for the NAMEATTR field. This tells the system that NAMEATTR is a P-field.
One way an RPG program might load a value into a P-field is by assigning a hexadecimal literal, like this:
nameattr = x'28';
The hex 28 value causes the field to blink on a dumb terminal and to be displayed in red on a not-quite-so-dumb terminal. That's not obvious enough. The source code will be more readable if we assign a named constant to the P-field, like this:
D Blink C Const(x'28')
NameAttr = Blink;
But the P-field value does not have to be hard-coded in the program's source code. It could be stored in a file or data area, passed into a program through a parameter, assigned a value according to user input, and so on.
P-fields are a superior alternative to indicators. Using P-fields with named constants that represent display attributes results in clearer code. P-fields can be stored in external objects like files and data areas or passed to a program through parameters.
However, that does not mean we should use P-fields only. Having to create a P-field for every data field on a display can get unwieldy. If a field always has a certain color or display attribute (it's always underlined, for example), it may not be worth the trouble to use a P-field. But for those times when you need more flexibility, P-fields are the way to go.
Monday, October 1, 2007
Brainstorm:
Brainstorming is a technique used to quickly generate a quantity of creative or original ideas on or about a process, problem, product, or service. Brainstorming can be used to:
· Develop a vision
· Review inputs, outputs, and flows of existing processes
· Create a list of products or services
· Eliminate wasteful and redundant work activities
· Reengineer a process, product, or service
· Design a new or improved process
· Establish standards, guidelines, or measures
· Identify the internal and external customers served
· Improve the work environment
· Gather data for use with other tools
A brainstorming session begins with a facilitator establishing basic ground rules and a code of conduct. Typical brainstorming rules state that all members have an equal opportunity to participate, there is no criticism or pulling rank, people should think creatively, no idea will be treated as insignificant, and there should be only one conversation at a time. Members need to be active participants, willing to share their ideas, opinions, concerns, issues, and experiences.
Next the team agrees on the topic to be brainstormed and whether to give ideas verbally or written on individual index cards, or any other easily manipulated medium. Either a structured (round table) or unstructured (free-flowing) approach is selected. Ideas should be generated quickly (5-15minutes) and are recorded clearly on a flipchart or board. The process stops when ideas become redundant or infrequent. Recorded ideas are reviewed for duplication and clarification, and eliminated when necessary. Remaining ideas are then evaluated with an open mind and may be used with the affinity diagram, nominal group technique, or cause-and-effect diagram.
· Develop a vision
· Review inputs, outputs, and flows of existing processes
· Create a list of products or services
· Eliminate wasteful and redundant work activities
· Reengineer a process, product, or service
· Design a new or improved process
· Establish standards, guidelines, or measures
· Identify the internal and external customers served
· Improve the work environment
· Gather data for use with other tools
A brainstorming session begins with a facilitator establishing basic ground rules and a code of conduct. Typical brainstorming rules state that all members have an equal opportunity to participate, there is no criticism or pulling rank, people should think creatively, no idea will be treated as insignificant, and there should be only one conversation at a time. Members need to be active participants, willing to share their ideas, opinions, concerns, issues, and experiences.
Next the team agrees on the topic to be brainstormed and whether to give ideas verbally or written on individual index cards, or any other easily manipulated medium. Either a structured (round table) or unstructured (free-flowing) approach is selected. Ideas should be generated quickly (5-15minutes) and are recorded clearly on a flipchart or board. The process stops when ideas become redundant or infrequent. Recorded ideas are reviewed for duplication and clarification, and eliminated when necessary. Remaining ideas are then evaluated with an open mind and may be used with the affinity diagram, nominal group technique, or cause-and-effect diagram.
SQL Technique:
Extract ONLY n Rows from a table.
To limit the amount of results that a query may retrieve, the “FETCH FIRST N ROWS ONLY” is a useful technique:
SELECT * FROM TABLE_NAME
FETCH FIRST 10 ROWS ONLY
The last clause ensures that only 10 rows are fetched.
Method to simulate a "right-justify" for character data using SQL
There is no "right-justify" string function built into SQL, but it can still be done: Taking a character string of variable size and right-justifying within a target column
containing a maximum of 12 characters. The example below does a bit more but it illustrates well what can be done, effectively concatenating blanks (up to 12) for a length of 12 - the length of the source column.
INSERT INTO TARGET_TABLE
SITE_CODE_RIGHT_JUSTIFED
SELECT
SUBSTR(' ', 1, 12 -
LENGTH( TRIM( CHAR_COLUMN_NAME)))
|| TRIM( CHAR_COLUMN_NAME )
FROM TABLE
FROM SOURCE_DATA
To limit the amount of results that a query may retrieve, the “FETCH FIRST N ROWS ONLY” is a useful technique:
SELECT * FROM TABLE_NAME
FETCH FIRST 10 ROWS ONLY
The last clause ensures that only 10 rows are fetched.
Method to simulate a "right-justify" for character data using SQL
There is no "right-justify" string function built into SQL, but it can still be done: Taking a character string of variable size and right-justifying within a target column
containing a maximum of 12 characters. The example below does a bit more but it illustrates well what can be done, effectively concatenating blanks (up to 12) for a length of 12 - the length of the source column.
INSERT INTO TARGET_TABLE
SITE_CODE_RIGHT_JUSTIFED
SELECT
SUBSTR(' ', 1, 12 -
LENGTH( TRIM( CHAR_COLUMN_NAME)))
|| TRIM( CHAR_COLUMN_NAME )
FROM TABLE
FROM SOURCE_DATA
Agile Software Development Method:
Agile Software Development is a conceptual framework for undertaking software engineering projects that embraces and promotes evolutionary change throughout the entire life-cycle of the project. There are a number of agile software development methods; most attempt to minimize risk by developing software in short time boxes, called iterations, which typically last one to four weeks. An agile software project intends to be capable of releasing new software at the end of every iteration particularly when the software is web-based and can be released easily.
Agile methods emphasize real-time communication, preferably face-to-face, over written documents. Agile methods produce very little written documentation relative to other methods.
Principles behind Agile methods
Some of the principles behind the Agile Manifesto are:
· Customer satisfaction by rapid, continuous delivery of useful software
· Working software is delivered frequently (weeks rather than months)
· Working software is the principal measure of progress
· Even late changes in requirements are welcomed
· Simplicity
· Regular adaptation to changing circumstances
Suitability of Agile methods
From a product perspective, agile methods are more suitable when requirements are emergent and rapidly changing; they are less suitable for systems that have high criticality, reliability and safety requirements.
The most important factor is probably project size. As size grows, face-to-face communication becomes more difficult. Therefore, most agile methods are more suitable for projects with small teams, with fewer than 20 to 40 people.
Agile development is expected to be particularly suitable for teams facing unpredictable or rapidly changing requirements.
Agile methods
Some of the well-known agile software development methods:
· Extreme Programming (XP)
· Scrum
· Agile Modeling
· Adaptive Software Development (ASD)
· Crystal Clear and Other Crystal Methodology
· Dynamic Systems Development Method (DSDM)
· Feature Driven Development (FDD)
· Lean software development
· Agile Unified Process (AUP)
Agile methods emphasize real-time communication, preferably face-to-face, over written documents. Agile methods produce very little written documentation relative to other methods.
Principles behind Agile methods
Some of the principles behind the Agile Manifesto are:
· Customer satisfaction by rapid, continuous delivery of useful software
· Working software is delivered frequently (weeks rather than months)
· Working software is the principal measure of progress
· Even late changes in requirements are welcomed
· Simplicity
· Regular adaptation to changing circumstances
Suitability of Agile methods
From a product perspective, agile methods are more suitable when requirements are emergent and rapidly changing; they are less suitable for systems that have high criticality, reliability and safety requirements.
The most important factor is probably project size. As size grows, face-to-face communication becomes more difficult. Therefore, most agile methods are more suitable for projects with small teams, with fewer than 20 to 40 people.
Agile development is expected to be particularly suitable for teams facing unpredictable or rapidly changing requirements.
Agile methods
Some of the well-known agile software development methods:
· Extreme Programming (XP)
· Scrum
· Agile Modeling
· Adaptive Software Development (ASD)
· Crystal Clear and Other Crystal Methodology
· Dynamic Systems Development Method (DSDM)
· Feature Driven Development (FDD)
· Lean software development
· Agile Unified Process (AUP)
Subscribe to:
Posts (Atom)