Tuesday, December 30, 2008
Excel Tip – Import a Text File to Excel:
2. In Text Import Wizard dialog box:
Step 1:
Select Delimited, US- ASCII and click Next.
Step 2:
Select Tab and click Next.
Step 3:
For each column select the Column Data Format and click Finish.
3. If delimiter is not present in the text file,
Step 1:
Select Fixed width and click Next.
Step 2:
By default, the data will be split at each spaces available in the data. If any changes are required, then click on the arrow and move it to the desired place of data separation and click next.
Step 3:
For each column select the Column Data Format and click Finish.
Monday, December 29, 2008
XML in 10 Points:
Structured data includes things like spreadsheets, address books, configuration parameters, financial transactions, and technical drawings. XML is a set of rules (you may also think of them as guidelines or conventions) for designing text formats that let you structure your data. XML is not a programming language, and you don't have to be a programmer to use it or learn it. XML makes it easy for a computer to generate data, read data, and ensure that the data structure is unambiguous. XML avoids common pitfalls in language design: it is extensible, platform-independent, and it supports internationalization and localization. XML is fully Unicode-compliant.
2. XML looks a bit like HTML
Like HTML, XML makes use of tags (words bracketed by '<' and '>') and attributes (of the form name="value"). While HTML specifies what each tag and attribute means, and often how the text between them will look in a browser, XML uses the tags only to delimit pieces of data, and leaves the interpretation of the data completely to the application that reads it. In other words, if you see "
" in an XML file, do not assume it is a paragraph. Depending on the context, it may be a price, a parameter, a person, a p... (and who says it has to be a word with a "p"?).
3. XML is text, but isn't meant to be read
Programs that produce spreadsheets, address books, and other structured data often store that data on disk, using either a binary or text format. One advantage of a text format is that it allows people, if necessary, to look at the data without the program that produced it; in a pinch, you can read a text format with your favorite text editor. Text formats also allow developers to more easily debug applications. Like HTML, XML files are text files that people shouldn't have to read, but may when the need arises. Compared to HTML, the rules for XML files allow fewer variations. A forgotten tag, or an attribute without quotes makes an XML file unusable, while in HTML such practice is often explicitly allowed. The official XML specification forbids applications from trying to second-guess the creator of a broken XML file; if the file is broken, an application has to stop right there and report an error.
4. XML is verbose by design
Since XML is a text format and it uses tags to delimit the data, XML files are nearly always larger than comparable binary formats. That was a conscious decision by the designers of XML. The advantages of a text format are evident (see point 3), and the disadvantages can usually be compensated at a different level. Disk space is less expensive than it used to be, and compression programs like zip and gzip can compress files very well and very fast. In addition, communication protocols such as modem protocols and HTTP/1.1, the core protocol of the Web, can compress data on the fly, saving bandwidth as effectively as a binary format.
5. XML is a family of technologies
XML 1.0 is the specification that defines what "tags" and "attributes" are. Beyond XML 1.0, "the XML family" is a growing set of modules that offer useful services to accomplish important and frequently demanded tasks. XLink describes a standard way to add hyperlinks to an XML file. XPointer is syntax in development for pointing to parts of an XML document. An XPointer is a bit like a URL, but instead of pointing to documents on the Web, it points to pieces of data inside an XML file. CSS, the style sheet language, is applicable to XML as it is to HTML. XSL is the advanced language for expressing style sheets. It is based on XSLT, a transformation language used for rearranging, adding and deleting tags and attributes. The DOM is a standard set of function calls for manipulating XML (and HTML) files from a programming language. XML Schemas 1 and 2 help developers to precisely define the structures of their own XML-based formats. There are several more modules and tools available or under development.
6. XML is new, but not that new
Development of XML started in 1996 and it has been a W3C Recommendation since February 1998, which may make you suspect that this is rather immature technology. In fact, the technology isn't very new. Before XML there was SGML, developed in the early '80s, an ISO standard since 1986, and widely used for large documentation projects. The development of HTML started in 1990. The designers of XML simply took the best parts of SGML, guided by the experience with HTML, and produced something that is no less powerful than SGML, and vastly more regular and simple to use. Some evolutions, however, are hard to distinguish from revolutions... And it must be said that while SGML is mostly used for technical documentation and much less for other kinds of data, with XML it is exactly the opposite.
7. XML leads HTML to XHTML
There is an important XML application that is a document format: W3C's XHTML, the successor to HTML. XHTML has many of the same elements as HTML. The syntax has been changed slightly to conform to the rules of XML. A format that is "XML-based" inherits the syntax from XML and restricts it in certain ways (e.g, XHTML allows "
", but not " " stands for "paragraph", and not for "price", "person", or anything else). " mean "paragraph" from this format or "person" from that one?). To eliminate name confusion when combining formats, XML provides a namespace mechanism. XSL and RDF are good examples of XML-based formats that use namespaces. XML Schema is designed to mirror this support for modularity at the level of defining XML document structures, by making it easy to combine two schemas to produce a third which covers a merged document structure.
8. XML is modular
XML allows you to define a new document format by combining and reusing other formats. Since two formats developed independently may have elements or attributes with the same name, care must be taken when combining those formats (does "
9. XML is the basis for RDF and the Semantic Web
W3C's Resource Description Framework (RDF) is an XML text format that supports resource description and metadata applications, such as music playlists, photo collections, and bibliographies. For example, RDF might let you identify people in a Web photo album using information from a personal contact list; then your mail client could automatically start a message to those people stating that their photos are on the Web. Just as HTML integrated documents, images, menu systems, and forms applications to launch the original Web, RDF provides tools to integrate even more, to make the Web a little bit more into a Semantic Web. Just like people need to have agreement on the meanings of the words they employ in their communication, computers need mechanisms for agreeing on the meanings of terms in order to communicate effectively. Formal descriptions of terms in a certain area (shopping or manufacturing, for example) are called ontologies and are a necessary part of the Semantic Web. RDF, ontologies, and the representation of meaning so that computers can help people do work are all topics of the Semantic Web Activity.
10. XML is license-free, platform-independent and well-supported
By choosing XML as the basis for a project, you gain access to a large and growing community of tools (one of which may already do what you need!) and engineers experienced in the technology. Opting for XML is a bit like choosing SQL for databases: you still have to build your own database and your own programs and procedures that manipulate it, but there are many tools available and many people who can help you. And since XML is license-free, you can build your own software around it without paying anybody anything. The large and growing support means that you are also not tied to a single vendor. XML isn't always the best solution, but it is always worth considering.
Sunday, December 28, 2008
Blind Ordering:
Thursday, December 25, 2008
Reply, then Reply All:
If you choose Reply, but then decide you want to include "all", you don't have to copy the reply you've created to the clipboard, close the email, and start over again this time pressing "Reply to All".
Instead, even if you first choose just "Reply" you can then click "Reply to All", and Notes will fill in the additional names for you.
Wednesday, December 24, 2008
Bill and Hold Basis:
The bill-and-hold basis is one method of revenue recognition. According to the Securities and Exchange Commission, it is the buyer's responsibility to request that a transaction be on a bill-and-hold basis and must have substantial business purposes in doing so. In addition to those criteria, any goods sold under this basis must be finished goods at the time of sale and not be available to fulfill any other orders.
Tuesday, December 23, 2008
Main components of Effective Presentation:
• Content
• Design
• Delivery
Each of these components has to be on the mark and they all have to work together, as well.
When writing your content, decide on two or three main points and make sure that everything else that you write leads to those points. Make your content logical, simple, and clear. Figure out what your audience needs and wants to know and tailor your content for the audience.
Regarding design, your number one concern is legibility. Don’t put too much text on a slide and keep it large enough to read easily. The text color should contrast highly with the background color. Then, make sure that your design complements your content. Your background and images shouldn’t detract from the content. Images should work to clarify text. The layout and size of text should bring important points to the fore.
Don’t forget a winning delivery. Engaging your audience with eye contact and your overall energy is important. Know your main points and emphasize them with your voice and the amount of time you spend on them. Two’s a party; three’s a crowd, they say. If you just read your slides, you’re putting PowerPoint between you and the audience and they’ll resent it. Instead, use the slides only as support for your presentation.
Beta Testing:
Sunday, December 21, 2008
Thursday, December 18, 2008
Rabbit Chase:
Bag Stuffer:
They're those little colorful slips of paper that have offers or coupons for savings that you often find in your bags after a day of shopping. These are a great way to promote your business and develop repeat customers.
They are very inexpensive to make and can be easily changed if a new promotion arises.
Queuing Theory:
Here are details of four queuing disciplines:
First in first out
This principle states that customers are served one at a time and that the customer that has been waiting the longest is served first
Last in first out
This principle also serves customers one at a time; however the customer with the shortest waiting time will be served first.
Processor sharing
Customers are served equally. Network capacity is shared between customers and they all effectively experience the same delay.
Priority
Customers with high priority are served first
Monday, December 15, 2008
Expanding one slide into two:
1. Place the cursor in the Outline tab of the Outline pane (not on the slide) at the end of the last line of text that you want on the first slide.
2. Press Enter.
3. On the Outline toolbar, click Promote until a New Slide icon appears in the Outline pane.
4. Type a title for the new slide.
5. Adjust the rest of the text as needed by clicking Demote or Promote on the Outline toolbar.
Friday, December 5, 2008
Lotus Notes – Take action from your address book:
From the Contacts view of your Personal Address Book (directory) you can select a name, or even better multiple names, and then click on either "Write Memo", "Schedule Meeting", or "Chat with Contact".
Notes will create the new document, and fill in the names for you.
Wednesday, December 3, 2008
Pull-Push Strategy:
In a "push" system the consumer does not request the product to be developed; it is "pushed" to the end-user by promotion. An example of this is a perfume product. Women do not request to smell a fragrance they never smelled before; it is simply "pushed" to them, through the right advertisement.
• Applied to that portion of the supply chain where demand uncertainty is relatively small
• Production & distribution decisions are based on long term forecasts
• Based on past orders received from retailer’s warehouse (may lead to Bullwhip effect)
• Inability to meet changing demand patterns
• Large and variable production batches
• Unacceptable service levels
• Excessive inventories due to the need for large safety stocks
In a "pull" system the consumer requests the product and "pulls" it through the delivery channel. An example of this is the car manufacturing company Ford Australia. Ford Australia only produces cars when they have been ordered by the customers.
• Applied to that portion of the supply chain where demand uncertainty is high
• Production and distribution are demand driven
• No inventory, response to specific orders
• Point of sale (POS) data comes in handy when shared with supply chain partners
• Decrease in lead time
• Difficult to implement
Tuesday, December 2, 2008
Find or Replace in all sheets of the workbook:
2. Press Ctrl+F to find or Ctrl+H to find and replace. (Note: Ctrl+F works only for a single sheet in Excel 97). In Excel 2002 and 2003, choose Sheet or Workbook from the within dropdown list (see the screenshot below).
Using wild cards in the text search:
Use * as a wild card for any number of characters, either before or after text, for example, searching for *CO will find both Cisco and Telco.
Use ? as a wild card for a single character, for example, searching for R?N will find Ron and Ran but not Rain.
To search for an asterisk, enter ~* in the search box.
Back Order:
Backorder Cost: A cost incurred by a business when it is unable to fill an order and must complete it later. A backorder cost can be discrete, as in the cost to replace a specific piece of inventory, or intangible, such as the effects of poor customer service. Backorder costs are usually computed and displayed on a per-unit basis.
Backorder costs include: costs of expediting, loss of customer goodwill and loss of sales revenues.
Backorder Date: Many vendors and retail businesses run into the problem of having backordered items, when they are waiting for the Manufacturer of a certain product(s) to deliver the expected goods. The manufacturer will give the vendor an expected date as to when the backordered item should be received. This date then becomes the backorder date for that specific item(s).
Sunday, November 30, 2008
Preventing Job logs:
Batch Job (BCHJOB),
Submit Job (SBMJOB),
Change Job (CHGJOB),
Create Job Description (CRTJOBD), or
Change Job Description (CHGJOBD) command.
If you specify *NOLIST for the message text value of the LOG parameter, the job log is not produced at the end of a job unless the job end code is 20 or greater. If the job end is 20 or greater, the job log is produced. For an interactive job, the value specified for the LOG parameter on the SIGNOFF command takes precedence over the LOG parameter value specified for the job.
Wednesday, November 26, 2008
Lotus Notes – Paragraph Styling:
The first thing you need to do is create the new style(s) you want to use. Begin by typing out a few sentences and then apply the formatting choices (font, spacing, colour, etc) that you want to use in the future. Once you have things looking the way you want, select the text and press ALT+ENTER to bring up the Text Properties Box. Click on the last tab, and click Create Style, then enter the name you wish to use.
Now any time you want to apply your awesome new style you can do so from either a) the menu "Text - Apply Style", b) the Styles tab of the Properties Box (shown above), or c) By pressing F11 to cycle through the available styles.
Changing the Name of the Cell Comment’s Author:
To change or cancel the name of the Comment's author:
1. From the Tools menu, select Options, and then select the General tab.
2. In User name text box, change or clear the user name.
Monday, November 24, 2008
Pugh Matrix:
It is a scoring matrix used for concept selection, in which options are assigned scores relative to criteria. The selection is made based on the consolidated scores. Before you start your detailed design you must have many options so that you choose the best out of them.
This tool is also known as 'Criteria Based Matrix’.
The Pugh matrix is a tool used to facilitate a disciplined, team-based process for concept generation and selection. Several concepts are evaluated according to their strengths and weaknesses against a reference concept called the datum (base concept). The datum is the best current concept at each iteration of the matrix.
The Pugh matrix allows you to
1. Compare different concepts
2. Create strong alternative concepts from weaker concepts
3. Arrive at an optimum concept that may be a hybrid or variant of the best of other concepts
The Pugh matrix encourages comparison of several different concepts against a base concept, creating stronger concepts and eliminating weaker ones until an optimal concept finally is reached. Also, the Pugh matrix is useful because it does not require a great amount of quantitative data on the design concepts, which generally is not available at this point in the process.
Sunday, November 23, 2008
American National Standards Institute (ANSI):
ANSI was formed in 1918 when five engineering societies and three government agencies founded the American Engineering Standards Committee (AESC). The AESC became the American Standards Association (ASA) in 1928. In 1966, the ASA was reorganized and became the United States of America Standards Institute (USASI). The present name was adopted in 1969.
ANSI's membership comprises government agencies, organizations, corporations, academic and international bodies, and individuals. In total, the Institute represents the interests of more than 125,000 companies and 3.5 million professionals.
Though ANSI itself does not develop standards, the Institute facilitates the development of American National Standards, also known as ANS, by accrediting the procedures of standards developing organizations. ANSI accreditation signifies that the procedures used by standards setting organizations meet the Institute's requirements for openness, balance, consensus, and due process.
The Institute is the official U.S. representative to the two major international standards organizations, the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), via the U.S. National Committee (USNC). ANSI participates in almost the entire technical program of both the ISO and the IEC, and administers many key committees and subgroups.
Friday, November 21, 2008
Analog, Digital and HDTV:
This system has worked pretty well for a long time, but it has some limitations:
• Conventional CRT sets display around 480 visible lines of pixels. Broadcasters have been sending signals that work well with this resolution for years, and they can't fit enough resolution to fill a huge television into the analog signal.
• Analog pictures are interlaced -- a CRT's electron gun paints only half the lines for each pass down the screen. On some TVs, interlacing makes the picture flicker.
• Converting video to analog format lowers its quality.
Broadcasting is currently changing to digital television (DTV). A digital signal transmits the information for video and sound as ones and zeros instead of as a wave. For over-the-air broadcasting, DTV will generally use the UHF portion of the radio spectrum with a 6 MHz bandwidth, just like analog TV signals do.
DTV has several advantages:
• The picture, even when displayed on a small TV, is better quality.
• A digital signal can support a higher resolution, so the picture will still look good when shown on a larger TV screen.
• The video can be progressive rather than interlaced -- the screen shows the entire picture for every frame instead of every other line of pixels.
• TV stations can broadcast several signals using the same bandwidth. This is called multicasting.
• If broadcasters choose to, they can include interactive content or additional information with the DTV signal.
HDTV is simply the highest of all the DTV standards. The lowest quality digital format in HDTV is about the same as the highest quality an analog TV can display. But whether you see a high-definition picture and hear the accompanying Dolby Digital® sound depends on two things. First, the station has to be broadcasting a high-definition signal. Second, you have to have the right equipment to receive and view it.
Thursday, November 20, 2008
Excel Tip – Reducing the used area:
Reducing the size of the used area also reduces the size of the workbook.
To reduce the used area:
1. Find the last cell that contains data in the sheet.
2. Delete all rows after this cell, as well as the columns to the right of the cell that do not contain data.
3. Press Ctrl+S to save the file. The address of the last cell in the used area is updated when the file is saved.
Tuesday, November 18, 2008
AJAX:
AJAX, is a group of interrelated web development techniques used for creating interactive web applications or rich Internet applications. With Ajax, web applications can retrieve data from the server asynchronously in the background without interfering with the display and behavior of the existing page.
Advantages
• In many cases, the pages on a website consist of much content that is common between them. Using traditional methods, that content would have to be reloaded on every request. However, using Ajax, a web application can request only the content that needs to be updated, thus drastically reducing bandwidth usage and load time.
• The use of asynchronous requests allows the client's Web browser UI to be more interactive and to respond quickly to inputs, and sections of pages can also be reloaded individually. Users may perceive the application to be faster or more responsive, even if the application has not changed on the server side.
• The use of Ajax can reduce connections to the server, since scripts and style sheets only have to be requested once.
Monday, November 17, 2008
Process Acceptance Certificate:
Incomplete tasks should be recorded here as should the degree of risk to which these shortcomings are now exposing the business. Based upon that information, the decision can be taken as to whether the new or changed process should be released into the live environment.
Sunday, November 16, 2008
Automated Clearing House:
ACH credit transfers include direct deposit payroll and vendor payments. ACH direct debit transfers include consumer payments on insurance premiums, mortgage loans, and other kinds of bills. Businesses are also increasingly using ACH to collect from customers online, rather than accepting credit or debit cards.
Uses of the ACH payment system
• Debit card transactions
• Direct deposit of payroll, Social Security and other government benefits, and tax refunds
• Direct debit payment of consumer bills such as mortgages, loans, utility bills, and insurance premiums, rents, and any other regular payment.
• Business-to-business (B2B) payments
• E-commerce payments
• Federal, state, and local tax payments
• Bank Treasury management departments sell this service to business and government customers
Wednesday, November 12, 2008
DB2 – Buffer Pool:
By default, applications use the buffer pool called IBMDEFAULTBP, which is created when the database is created. The DB2 database configuration parameter BUFFPAGE controls the size of a buffer pool when the value of NPAGES is -1 for that buffer pool in the SYSCAT.BUFFERPOOLS catalog table. Otherwise the BUFFPAGE parameter is ignored, and the buffer pool is created with the number of pages specified by the NPAGES parameter.
Tuesday, November 11, 2008
Add Recipients to Group in Address Book:
You will be presented with the following dialog box where you enter the group's name, type (normally you just leave this as Mail only), description, and select/de-select with members you want the group to contain.
When you press OK, Lotus Notes will automatically create a new mailing group (some people call them distribution lists) in your Personal Address Book, which you can access from the "Groups" view.
Now when creating an email or calendar entry, you can simply enter the group name instead of typing in all the names individually. For example, if I named the group above "IBM Executive Team", then I could enter than in the To field...
and when I press F9 to refresh the document, the group name will be replaced with the names of the members.
Monday, November 10, 2008
Affiliated Retailer:
2. Independent retailer who affiliates with other independent retailers under a common trade name for merchandising purposes. A group of such independent retailers will advertise under this common trade name.
Well known examples of affiliated groups are SUPERVALU, Certified Grocers of California and Independent Grocers Association in the United States.
Sunday, November 9, 2008
Excel Tip – Move to the last (or first) cell in a range:
• Vertically from bottom to top, press Ctrl+Up Arrow.
• Horizontally from left to right, press Ctrl+Right Arrow.
• Horizontally from right to left, press Ctrl+Left Arrow.
Using the mouse
Double-click one edge of the selected cell when the mouse image changes to four directional arrows.
Thursday, November 6, 2008
Day Light Saving (DST):
The main purpose of Daylight Saving Time (called "Summer Time" in many places in the world) is to make better use of daylight. We change our clocks during the summer months to move an hour of daylight from the morning to the evening. Countries have different change dates.
According to some sources, DST saves energy. Studies done by the U.S. Department of Transportation in 1975 showed that Daylight Saving Time trims the entire country's electricity usage by a small but significant amount, about one percent each day, because less electricity is used for lighting and appliances. Similarly, in New Zealand, power companies have found that power usage decreases 3.5 percent when daylight saving starts. In the first week, peak evening consumption commonly drops around five percent.
There may also be an economic benefit to DST, as daylight evening hours encourage people to go out and shop, potentially spurring economic growth.
For more information please visit
http://www.webexhibits.org/daylightsaving/index.html
Wednesday, November 5, 2008
Advanced-Shipping Notice:
In the EDI X12 system, it is known as the EDI 856 document. The ASN can be used to list the contents of a shipment of goods as well as additional information relating to the shipment, such as order information, product description, physical characteristics, type of packaging, marking, carrier information, and configuration of goods within the transportation equipment. The ASN enables the sender to describe the contents and configuration of a shipment in various levels of detail and provides an ordered flexibility to convey information
Tuesday, November 4, 2008
SPAM, SPIM and SPIT:
SpIM is a term that has recently been coined to refer to spam sent via instant messenger programs, such as AOL Instant Messenger, MSN Messenger and ICQ. Someone who sends instant messenger spam (SPiM) is referred to as a spimmer, again a play on the term spammer.
SPIT (Spam over Internet Telephony) is one of the foreseen future forms of spamming that Internet authorities are preparing for today. With the increasing use and dependence on the Internet for communications and data transfer, malicious software programmers have taken advantage by creating VoIP bots with the ability to harvest data and advertise massively at a very small cost. These advertising methods include email spams, SPIMS or spams over instant messaging applications, malicious bots that generate pop up ads, initiate redirects, etc.
Monday, November 3, 2008
Poisson distribution:
The Poisson distribution is determined by one parameter, lambda. The distribution function for the Poisson distribution is f(x) = exp(-1*lambda) lambda^x / x!
Sunday, November 2, 2008
Inventory Turnover:
Also Known As: Turns, Stock Turns, Stock Turnover
Thursday, October 30, 2008
Quickly create groups in Lotus Notes:
For example, if I select people in my family, and then choose Tools - Copy Into New Group
Notes create a new Group document, with the values of each contact filled in automatically. All we need to do now is give the group a name, and save and close.
This is very useful if you often find that you are sending emails to the same group of people.
Wednesday, October 29, 2008
Make Subfile Page to retain its page:
Code
Using PDM, in the control section of your display file, add in the line
@pag 4 0H SFLRCDNBR
@pag is in the NAME column, the 4 is the length, the 0 is the decimal position and the SFLRCDNBR is in the functions column.
In your program, initialize @pag to 1.
When you select the line to change, z-add the rrn to @pag, and your program will return you to the subfile page you were on.
Inventory:
There are three basic reasons for keeping an inventory:
1. Time - The time lags present in the supply chain, from supplier to user at every stage, requires that you maintain certain amount of inventory to use in this "lead time"
2. Uncertainty - Inventories are maintained as buffers to meet uncertainties in demand, supply and movements of goods.
3. Economies of scale - Ideal condition of "one unit at a time at a place where user needs it, when he needs it" principle tends to incur lots of costs in terms of logistics. So bulk buying, movement and storing brings in economies of scale, thus inventory.
All these stock reasons can apply to any owner or product stage.
• Buffer stock is held in individual workstations against the possibility that the upstream workstation may be a little delayed in long setup or change-over time. This stock is then used while that change-over is happening.
• Distressed inventory is inventory whose potential to be sold at a normal cost has or will soon pass. In certain industries it could also mean that the stock is or will soon be impossible to sell. Examples of distressed inventory include products that have reached its expiry date, or has reached a date in advance of expiry at which the planned market will no longer purchase it (e.g. 3 months left to expiry), clothing that is defective or out of fashion, and old newspapers or magazines. It also includes computer or consumer-electronic equipment that is obsolescent or discontinued and whose manufacturer is unable to support it.
Thursday, October 23, 2008
Pearson’s Correlation:
Positive correlation indicates that both variables increase or decrease together, whereas negative correlation indicates that as one variable increases, so the other decreases, and vice versa.
Wednesday, October 22, 2008
Easy way to Sort Subfile data:
Maybe so. The circumstances where this is effective are limited, for sure, but if your requirements fit, then using SORTA with a group field can be the simplest way and often a faster alternative than other methods you may have tried.
First of all, what's a group field? It's a field in a data structure that is broken down into smaller subfields. For example, group field SflData might be made up of information about products (name, price, quantity) by using the Overlay keyword, such as:
D SflDS Ds Inz
D SflData Like(SflRecData)
D Dim(999)
D Name Like(ProdDS)
D Overlay(SflData)
D Price Like(SellPr)
D Overlay(SflData:*Next)
D Qty Like(STOH)
D Overlay(SflData:*Next)
The effect is similar to nested data structures, except without the requirement to use qualified names. (Likewise, there are many limitations on group fields because of the lack of name qualification.) One additional thing that's nice about group fields compared to nested DSs is that we can use SORTA against any of the subfields in a group field array.
So this means if I wanted to sort the data in the SflData array by product name, I could do that with the following statement: SortA Name;. Much simpler than any of those other options I mentioned above! Of course, in nearly all cases, it would require the use of the built-in function %SubArr (substring array) because I'm not likely to have filled up all 999 elements of SflData. Even so, the entire bit of logic to accomplish sorting this subfile data in the sequence of any of the three fields could be as simple as:
If SortByName;
SortA %SubArr(Name:1:Count);
ElseIf SortByQty;
SortA %SubArr(Qty:1:Count);
ElseIf SortByPrice;
SortA %SubArr(Price:1:Count);
EndIf;
This technique is very simple and in most cases quite a fast way to sort subfile data (or any other kind of repeating data). It does have significant limitations. For example, you can only sort on one subfield at a time. (Of course, you could group two subfields together if they happen to be adjacent in the subfile record.) Also, you must be able to retrieve and store all the data destined for the subfile into an array so that you can sort it all together. For some very large subfiles, that won't be practical. But for those occasions where it works, it couldn't get much simpler.
Tuesday, October 21, 2008
Drop Shipping:
Examples: To expand our product listing online, we use several suppliers that offer drop shipping.
Monday, October 20, 2008
Repeating Calendar entries in Lotus Notes:
Sunday, October 19, 2008
Conditional Insert in SQL:
Example:
if not exists (select 1 from table1 where key1 = ?) then
insert into table1
(key1, key2, key3, key4)
values (?, ?, ?, 1);
end if
As DB2 does not support dynamic scripting, this can be achieved by the following query.
insert into table1
(key1, key2, key3, key4)
Select ?,?,?,1
From SysDummy1
Where Not Exists
(Select 1
From table1
Where key1=?)
The question marks represent parameter markers (roughly equivalent to host variables in pre-compiled SQL.) Values need to be assigned to each of these markers before the statement can execute successfully.
Take note that SysDummy1 is a special IBM one row table that can be used as a trick for these one row operation situations! This is because inserting parameter values from a one row table is equivalent to the INSERT/VALUES statement. Placing the NOT EXISTS predicate in the WHERE clause instead of using an IF statement still allows us to condition if the row should be inserted by testing whether the row already exists.
As a side note, SysDummy1 resides in the SysIBM schema so it should be part of the library list when using the *SYS naming convention or fully qualified (SYSIBM.SysDummy1) when using the *SQL naming convention. Alternatively, if you have a one row table in your own schema it can be substituted for SYSDUMMY1 as well.
Thursday, October 16, 2008
Year 2038 Problem:
Most programs written in the C programming language are relatively immune to the Y2K problem, but suffer instead from the Year 2038 problem. This problem arises because most C programs use a library of routines called the standard time library . This library establishes a standard 4-byte format for the storage of time values, and also provides a number of functions for converting, displaying and calculating time values.
The standard 4-byte format assumes that the beginning of time is January 1, 1970, at 12:00:00 a.m. This value is 0. Any time/date value is expressed as the number of seconds following that zero value. So the value 919642718 is 919,642,718 seconds past 12:00:00 a.m. on January 1, 1970, which is Sunday, February 21, 1999, at 16:18:38 Pacific time (U.S.). This is a convenient format because if you subtract any two values, what you get is a number of seconds that is the time difference between them. Then you can use other functions in the library to determine how many minutes/hours/days/months/years have passed between the two times.
If you have read How Bits and Bytes Work, you know that a signed 4-byte integer has a maximum value of 2,147,483,647, and this is where the Year 2038 problem comes from. The maximum value of time before it rolls over to a negative (and invalid) value is 2,147,483,647, which translates into January 19, 2038. On this date, any C programs that use the standard time library will start to have problems with date calculations.
This problem is somewhat easier to fix than the Y2K problem on mainframes, fortunately. Well-written programs can simply be recompiled with a new version of the library that uses, for example, 8-byte values for the storage format. This is possible because the library encapsulates the whole time activity with its own time types and functions (unlike most mainframe programs, which did not standardize their date formats or calculations). So the Year 2038 problem should not be nearly as hard to fix as the Y2K problem was.
An alert reader was kind enough to point out that IBM PC hardware suffers from the Year 2116 problem. For a PC, the beginning of time starts at January 1, 1980, and increments by seconds in an unsigned 32-bit integer in a manner similar to UNIX time. By 2116, the integer overflows.
Windows NT uses a 64-bit integer to track time. However, it uses 100 nanoseconds as its increment and the beginning of time is January 1, 1601, so NT suffers from the Year 2184 problem.
On this page, Apple states that the Mac is okay out to the year 29,940!
Passion for Action (PFA):
PFA is a characteristic of highly Successful Companies as it permeates all activities at all levels of the business culture. An organization containing PFA will develop an Enterprise-Wide Current that continuously pulls the organization to its next performance level.
The concept was coined by Organizational Change Agent Consultant Rick Carangelo.
Wednesday, October 15, 2008
Bankruptcy Concept:
If you could read patiently and understand, it's a great knowledge!
Once there was a little island country. The land of this country was the tiny island itself. The total money in circulation was 2 dollars as there were only two pieces of 1 dollar coins circulating around.
1) There were 3 citizens living on this island country. A owned the land.
B and C each owned 1 dollar.
2) B decided to purchase the land from A for 1 dollar. So, now A and C own
1 dollar each while B owned a piece of land that is worth 1 dollar.
* The net asset of the country now = 3 dollars.
3) Now C thought that since there is only one piece of land in the country, and land is non producible asset, its value must definitely go up. So, he borrowed 1 dollar from A, and together with his own 1 dollar, he bought the land from B for 2 dollars.
*A has a loan to C of 1 dollar, so his net asset is 1 dollar.
* B sold his land and got 2 dollars, so his net asset is 2 dollars.
* C owned the piece of land worth 2 dollars but with his 1 dollar debt to A, his net residual asset is 1 dollar.
* Thus, the net asset of the country = 4 dollars.
4) A saw that the land he once owned has risen in value. He regretted having sold it. Luckily, he has a 1 dollar loan to C. He then borrowed 2 dollars from B and acquired the land back from C for 3 dollars. The payment is by 2 dollars cash (which he borrowed) and cancellation of the 1 dollar loan to C. As a result, A now owned a piece of land that is worth 3 dollars. But since he owed B 2 dollars, his net asset is 1 dollar.
* B loaned 2 dollars to A. So his net asset is 2 dollars.
* C now has the 2 coins. His net asset is also 2 dollars.
* The net asset of the country = 5 dollars. A bubble is building up.
(5) B saw that the value of land kept rising. He also wanted to own the land. So he bought the land from A for 4 dollars. The payment is by borrowing 2 dollars from C, and cancellation of his 2 dollars loan to A.
* As a result, A has got his debt cleared and he got the 2 coins. His net asset is 2 dollars.
* B owned a piece of land that is worth 4 dollars, but since he has a debt of 2 dollars with C, his net Asset is 2 dollars.
* C loaned 2 dollars to B, so his net asset is 2 dollars.
* The net asset of the country = 6 dollars; even though, the country has only one piece of land and 2 Dollars in circulation.
(6) Everybody has made money and everybody felt happy and prosperous.
(7) One day an evil wind blew, and an evil thought came to C's mind. "Hey, what if the land price stop going up, how could B repay my loan. There is only 2 dollars in circulation, and, I think after all the land that B owns is worth at most only 1 dollar, and no more."
(8) A also thought the same way.
(9) Nobody wanted to buy land anymore.
* So, in the end, A owns the 2 dollar coins, his net asset is 2 dollars.
* B owed C 2 dollars and the land he owned which he thought worth 4 dollars is now 1 dollar. So his net asset is only 1 dollar.
* C has a loan of 2 dollars to B. But it is a bad debt. Although his net asset is still 2 dollars, his Heart is palpitating.
* The net asset of the country = 3 dollars again.
(10) So, who has stolen the 3 dollars from the country ? Of course, before the bubble burst B thought his land was worth 4 dollars. Actually, right before the collapse, the net asset of the country was 6 dollars on paper. B's net asset is still 2 dollars, his heart is palpitating.
(11) B had no choice but to declare bankruptcy. C as to relinquish his 2 dollars bad debt to B, but in return he acquired the land which is worth 1 dollar now.
* A owns the 2 coins, his net asset is 2 dollars.
* B is bankrupt, his net asset is 0 dollar. ( he lost everything )
* C got no choice but end up with a land worth only 1 dollar
* The net asset of the country = 3 dollars.
************ **End of the story; BUT ************ ********* ******
There is however a redistribution of wealth. A is the winner, B is the loser, C is lucky that he is spared. A few points worth noting -
(1) When a bubble is building up, the debt of individuals to one another in a country is also building up.
(2) This story of the island is a closed system whereby there is no other country and hence no foreign debt. The worth of the asset can only be calculated using the island's own currency. Hence, there is no net loss.
(3) An over-damped system is assumed when the bubble burst, meaning the land's value did not go down to below 1 dollar.
(4) When the bubble burst, the fellow with cash is the winner.. The fellows having the land or extending loan to others are the losers. The asset could shrink or in worst case, they go bankrupt.
(5) If there is another citizen D either holding a dollar or another piece of land but refrains from taking part in the game, he will neither win nor lose. But he will see the value of his money or land go up and down like a see saw.
(6) When the bubble was in the growing phase, everybody made money.
(7) If you are smart and know that you are living in a growing bubble, it is worthwhile to borrow money (like A ) and take part in the game. But you must know when you should change everything back to cash.
(8) As in the case of land, the above phenomenon applies to stocks as well.
(9) The actual worth of land or stocks depend largely on psychology
Tuesday, October 14, 2008
Digital Signage:
Also Known As: Captive Audience Networks, Narrowcasting, Electronic Billboards, Electronic Display
Examples: Instead of cluttering our checkout counter with fliers or brochures of printed information on our value-added services, our retail store has a digital signage system with several displays of our staff actually performing these services for customers. These digita signs are strategically placed around the store and run certain services at particular times of the day.
Tuesday, October 7, 2008
Work IP Device-TAA (WRKIPDEV):
Enter the following command (WRKIPDEV) from Command prompt if TAATOOL available on the system.
Command:
TAATOOL/WRKIPDEV DEVTYPE(*PRT) OUTQ(*ALL/*ALL) OUTPUT(*PRINT)
Once the command is been executed check in spool file. This will give you a list of IP printers, by IP address, on your system with Dev/OutQ name.
If you want to view in display mode and not in spool file execute the below command without providing OUTPUT (*PRINT) value.
TAATOOL/WRKIPDEV DEVTYPE(*PRT) OUTQ(*ALL/*ALL)
Monday, October 6, 2008
Create Hotspot in Lotus Notes:
To begin, select the text you wish to turn into a hotspot.
Next choose Create - Hotspot - Link Hotspot.
This brings up the Properties Box, where you can enter the web address, or URL.
If you would like a larger dialog box to enter the information into, you can click on the formula icon and a dialog box will pop-up. This dialog box allows for some very advanced features such as adding Fields or @Functions, but I think most users will not need to use these.
The Hotspot Resource Link dialog box also provides you a "paste" icon , so if you already have the URL on your clipboard you can just click on this icon.
If you would like you can also choose to "Show Border around hotspot", this places a green box around the text where the hotspot exists. This border is only available to Lotus Notes users.
Instead of using the borders, I like to underline my hotspots so they appear similar to links found on web pages. To do this, place your cursor anywhere in the hotspot text (you don't have to highlight the whole thing) and press CTRL+U to underline. (or use the toolbar icon)
If you prefer to use your keyboard as opposed to menus, after selecting the text you want to turn into a hotspot, press ALT+C+H+L.
Sunday, October 5, 2008
Thursday, October 2, 2008
Create physical files on the fly:
This article demonstrates how you can take advantage of QShell from a CL program to create a PF in which you can embed the source code, including the field definitions, inside the code of the CL program itself.
The trick to producing a PF on the fly from CL is QShell's db2 utility. This utility runs an SQL statement that's passed as a parameter. Because QShell commands can be run from CL's STRQSH command, embedding an SQL statement in a CL program is relatively easy. For example:
PGM
STRQSH CMD('db2 "create table SOMELIB.SOMEFILE ( +
field1 decimal(5,0), +
field2 char(30), +
field3 date +
)"')
ENDPGM
Tuesday, September 30, 2008
Verify the JDE Version:
From any menu, type 97 on the command line.
Under the column labeled Release Level, find the highest letter/number combination. For example A8.1.
Monday, September 29, 2008
Category Killer:
Also Known As: Big Box Store
Examples: Best Buy is an example of an electronics category killer.
Sunday, September 28, 2008
How to stop Procrastinating:
• Harold Taylor defines procrastination as the intentional and habitual postponement of an important task that should be done now.
• Understand the cause for procrastination, then develop strategies to fix it.
• Recognize the difference between an appropriate decision to delay, and an irrational postponement without justification.
• Fix procrastination by working on a) tasks and b) your environment:
TASK STRATEGIES
Unpleasant tasks
• Unpleasant tasks rarely turn out to be as bad as you think.
• Complete these tasks first. Schedule them for early in the day. Give yourself a reward for doing them.
Complex Projects
• Something looms ahead of you: starting a small business, getting a job, preparing the annual budget. The job is too big or will take too long to do now, so you put it off.
• Break large jobs into smaller, more manageable tasks. Plan and complete a start-up task, no matter how small.
Indecision
• People delay because they can't make up their minds.
• Determine a time for making a decision and the criteria for making it. Share your deadline with someone else.
Fear of failure (lack of self confidence)
• People don't want to face the consequences of failure, so they delay. (Some people suffer from fear of success too!)
• Develop a clear mental picture of the completed task and how you will feel at that time. Maintain a focus on the end result, not just the process. Remind yourself how good you'll feel when you're finished.
Lack of interest
• You are tired or lazy. You're just not very interested in the task.
• Reward yourself for accomplishments. Go out for special lunches when major projects are completed. If you don't earn the reward, don't take it.
• Schedule the task for when you will be at your peak.
Perfectionism
• People delay because they want to get the project perfect.
• Set deadlines for yourself. Tell other people your deadlines and encourage them to check up on you.
• Maintain your high standards, but recognize that sometimes 80% for you may well be 100% for someone else. Don't spend hours conducting a detailed cost breakdown when a rough estimate would suffice.
Hostility towards a boss
• People delay because they don't like the person who assigned the task.
• Review with your boss what exactly is needed. Clarify the expectations.
• Make a game out of unpleasant tasks. Give yourself points, or do a running commentary on yourself as you do the task.
Distraction, lack of focus
• Sometimes losing concentration causes delays.
• Create a to-do list with priorities.
• Block your time for projects.
• As you get distracted from a work project, make a rule that you are not allowed to move out of your chair, make a call, surf the net, pick up a book etc. until you return to your task.
• Complete something. Make a very small task for yourself and finish it. Very small. Then, make another one.
ENVIRONMENT STRATEGIES
• Tailor your environment for work. Close your door, clean up the clutter on your desk.
• Remove distractions such as water coolers, snacks, in-boxes, coffee machines and magazine racks.
• If you work at home, treat your office as an office. Don't go out to lunch before lunchtime or watch television before the end of the day.
• Tell your family that you are not to be disturbed in your home office.
Thursday, September 25, 2008
SQL Case Expression:
Use:
Multiple updates based on multiple conditions, in one pass could be done by SQL case expressions:
E.g.:
The following two SQL statements can be combined into one. The single statement may run faster, especially against a large file, since it makes only one pass.
Update filename set field1 = 'Y1' where field1 = 'X1'
Update filename set field2 = 'Y2' where field2 = 'X2'
Single statement:
Update filename set
field1 = CASE
When field1 = 'X1' then 'Y1'
Else field1
END,
field2 = CASE
When field2 = 'X2' then 'Y2'
Else field2
END
Where field1 = 'X1' or field2 = 'X2'
Wednesday, September 24, 2008
Conflict Resolution:
The fact that conflict exists, however, is not necessarily a bad thing: As long as it is resolved effectively, it can lead to personal and professional growth.
In many cases, effective conflict resolution skills can make the difference between positive and negative outcomes.
Negative Effects:
However, if conflict is not handled effectively, the results can be damaging. Conflicting goals can quickly turn into,
• Personal dislike.
• Teamwork breaks down.
• Talent is wastage of people.
Different Styles for different situations.
Once you understand the different styles, you can use them to think about the most appropriate approach (or mixture of approaches) for the situation you're in. You can also think about your own instinctive approach, and learn how you need to change this if necessary.
Competitive: People who tend towards a competitive style take a firm stand, and know what they want. They usually operate from a position of power, drawn from things like position, rank, expertise, or persuasive ability. This style can be useful when there is an emergency and a decision needs to be make fast; when the decision is unpopular; or when defending against someone who is trying to exploit the situation selfishly. However it can leave people feeling bruised, unsatisfied and resentful when used in less urgent situations.
Collaborative: People tending towards a collaborative style try to meet the needs of all people involved. These people can be highly assertive but unlike the competitor, they cooperate effectively and acknowledge that everyone is important. This style is useful when a you need to bring together a variety of viewpoints to get the best solution; when there have been previous conflicts in the group; or when the situation is too important for a simple trade-off.
Compromising: People who prefer a compromising style try to find a solution that will at least partially satisfy everyone. Everyone is expected to give up something, and the compromiser him- or herself also expects to relinquish something. Compromise is useful when the cost of conflict is higher than the cost of losing ground, when equal strength opponents are at a standstill and when there is a deadline looming.
Accommodating: This style indicates a willingness to meet the needs of others at the expense of the person’s own needs. The accommodator often knows when to give in to others, but can be persuaded to surrender a position even when it is not warranted. This person is not assertive but is highly cooperative. Accommodation is appropriate when the issues matter more to the other party, when peace is more valuable than winning, or when you want to be in a position to collect on this “favor” you gave. However people may not return favors, and overall this approach is unlikely to give the best outcomes.
Avoiding: People tending towards this style seek to evade the conflict entirely. This style is typified by delegating controversial decisions, accepting default decisions, and not wanting to hurt anyone’s feelings. It can be appropriate when victory is impossible, when the controversy is trivial, or when someone else is in a better position to solve the problem. However in many situations this is a weak and ineffective approach to take.
Tips for better conflict Resolution:
• Make sure that good relationships are the first priority: As far as possible, make sure that you treat the other calmly and that you try to build mutual respect. Do your best to be courteous to one-another and remain constructive under pressure;
• Keep people and problems separate: Recognize that in many cases the other person is not just "being difficult" – real and valid differences can lie behind conflictive positions. By separating the problem from the person, real issues can be debated without damaging working relationships;
• Pay attention to the interests that are being presented: By listening carefully you'll most-likely understand why the person is adopting his or her position;
• Listen first; talk second: To solve a problem effectively you have to understand where the other person is coming from before defending your own position;
• Set out the “Facts”: Agree and establish the objective, observable elements that will have an impact on the decision; and
• Explore options together: Be open to the idea that a third position may exist, and that you can get to this idea jointly.
Tuesday, September 23, 2008
Delivery Option in Lotus Notes Mail:
Setting the importance of the mail, Mood stamps
Setting various Delivery reports.
Auto spell check, Return Receipt & Encryption.
Setting Expiration and Archiving stamp for the recipient.
Another handy option we have in Advanced Tab which controls the Reply option of a mail. By putting a Person/Group name in Delivery Option the recipient will see whom he has to Reply and it automatically Replies to that person when he selects “Reply” option.
To know whether a mail has RR, go to document property and check for a field named “Return Receipt”. If the value of the field is “1” that means it has Return Receipt option enabled. Also to stop a Return Receipt, immediately after opening the mail you need to go to Outbox view just under Inbox option and delete that mail.
Another feature is “Return receipt” which let you know when the recipient has Opened/Marked a mail as “Unread”.
Another very important feature is “Prevent Copying”. When you do not want the recipient to copy your mail or Forward to someone you can select this option.
Monday, September 22, 2008
Replace the Value of the field in a particular position in SQL:
Syntax:
REPLACE (string_expression1, string_expression2, string_expression3)
string_expression1
Is the string expression to be searched. string_expression1 can be of a character or binary data type.
string_expression2
Is the substring to be found. string_expression2 can be of a character or binary data type.
string_expression3
Is the replacement string. string_expression3 can be of a character or binary data type.
Example:
UPDATE kgipkemp set kmfld1 = REPLACE(kmfld1,substr(kmfld1,21,6), '080901' )
Sunday, September 21, 2008
Display Status Message in Reverse Image:
DCL VAR(&REVERSE) TYPE(*CHAR) LEN(1) VALUE(X'21')
DCL VAR(&NORMAL) TYPE(*CHAR) LEN(1) VALUE(X'20')
SNDPGMMSG MSGID(CPF9898) MSGF(QCPFMSG) +
MSGDTA(&REVERSE *CAT &MSG *CAT &NORMAL) +
TOPGMQ(*EXT) MSGTYPE(*STATUS)
Thursday, September 18, 2008
BIOS:
The primary function of the BIOS is to identify and initialize system component hardware (such as the video display card, hard disk, and floppy disk) and some other hardware devices. This is to prepare the machine into a known low capability state, so other software programs stored on various media can be loaded, executed, and given control of the PC. This process is known as booting, or booting up, which is short for bootstrapping.
Major BIOS vendors include American Megatrends (AMI), General Software, Insyde Software, and Phoenix Technologies.
Comp Sales:
Also Known As: Same-Store Sales, Comparable Store Sales, Comp-Store
Examples: Best Buy showed an impressive comp-store sales growth of 5.9% last quarter which was fueled by strength in flat-panel TVs, video gaming hardware and notebook computers.
Wednesday, September 17, 2008
RSS Feed:
RSS solves a problem for people who regularly use the web. It allows you to easily stay informed by retrieving the latest content from the sites you are interested in. You save time by not needing to visit each site individually. You ensure your privacy, by not needing to join each site's email newsletter.
RSS feeds can be read using software called an "RSS reader," "feed reader," or an "aggregator," which can be web-based or desktop-based.
The user subscribes to a feed by entering the feed's link into the reader or by clicking an RSS icon in a browser that initiates the subscription process. The RSS reader checks the user's subscribed feeds regularly for new work, downloads any updates that it finds, and provides a user interface to monitor and read the feeds.
Monday, September 15, 2008
Find Data in a Multi-Member file:
Key in FNDSTRPDM + F4. Options are self-explanatory.
Option member allow user to key in "*ALL" and will search through all members for the strings keyed.
Allows user to display, print, and edit records when string is found.
Sunday, September 14, 2008
Size Matters:
With the Properties Box open, switch to the second tab "i" for Information. There you can see the size of your mail file.
Thursday, September 11, 2008
Break-Even Point:
Formula:
Break-Even Point ($) = Fixed Costs ÷ Gross Margin Percentage
Also Known As: Breakeven Analysis
Examples: Our retail store buys widgets for $15 each, marks them up and sells them for $30. Our monthly expenses (fixed costs) are $10,000. This means our breakeven point would be $20,000 or 667 units.
$10,000 ÷ (15/30) = $20,000
$20,000 ÷ $30 = 667
Wednesday, September 10, 2008
Nominal Group Technique:
When to use this technique:
• When some group members are much more vocal than others.
• When some group members think better in silence.
• When there is concern about some members not participating.
• When the group does not easily generate quantities of ideas.
• When all or some group members are new to the team.
• When the issue is controversial or there is heated conflict.
As with any technique, there are advantages and disadvantages. NGT is no exception. One major advantage of NGT is that it avoids two problems caused by group interaction. First, some members are reluctant to suggest ideas because they are concerned about being criticized. Second, some members are reluctant to create conflict in groups. (Many people want to maintain a pleasant climate.) NGT overcomes these problems. NGT has the clear advantage of minimizing differences and ensuring relatively equal participation. It may also, in many cases be a time-saving technique. Other advantages include producing a large number of ideas and providing a sense of closure that is often not found in less-structured group methods.
Major disadvantage of NGT is that the method lacks flexibility by only being able to deal with one problem at a time. Also, there must be a certain amount of conformity on the part of the members involved in NGT. Everyone must feel comfortable with the amount of structure involved. Another disadvantage is the amount of time needed to prepare for the activity. There is no spontaneity involved with this method. Facilities must be arranged and carefully planned. Opinions may not converge in the voting process, cross-fertilization, of ideas may be constrained, and the process may appear to be too mechanical.
Tuesday, September 9, 2008
Use SQL to remove extra spaces:
Run the following query to see what would happen.
select name,
replace(replace(replace(name,' ','<>'),'><',''),'<>',' ')
from qtemp/mydata
This is the output:
NAME REPLACE
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
So how does it work? The innermost REPLACE changes all blanks to a less-than greater-than pair. So, if there are three spaces between Joe and Smith, the innermost REPLACE returns Joe<><><>Smith.
The middle REPLACE changes all greater-than less-than pairs to the empty string, which removes them. Joe<><><>Smith becomes Joe<>Smith.
The outer REPLACE changes all less-than greater-than pairs to a single blank. Joe<>Smith becomes Joe Smith.
You do not have to use the less-than and greater-than symbols. Any two characters that are not used in the field will work.
Monday, September 8, 2008
How does a Firewall work:
Basically, a firewall, working closely with a router program, examines each network packet to determine whether to forward it toward its destination. A firewall also includes or works with a proxy server that makes network requests on behalf of workstation users. A firewall is often installed in a specially designated computer separate from the rest of the network so that no incoming request can get directly at private network resources.
There are a number of firewall screening methods. A simple one is to screen requests to make sure they come from acceptable (previously identified) domain name and Internet Protocol addresses. For mobile users, firewalls allow remote access in to the private network by the use of secure logon procedures and authentication certificates.
A number of companies make firewall products. Features include logging and reporting, automatic alarms at given thresholds of attack, and a graphical user interface for controlling the firewall.
Sunday, September 7, 2008
Unexplored User profile User Options:
When using the CRTUSRPRF, CHGUSRPRF, or CHGPRF command, one of the last parameters is User Options(USROPT).
The default value for USROPT is *NONE, so when we do not specify an alternate value, we get no special options for that user.
The alternate values we can specify include *CLKWD, *EXPERT, *ROLLKEY, *NOSTSMSG, *STSMSG, *HLPFULL, and *PRTMSG.
Here's an example of using the USROPT parameter.
CRTUSRPRF USRPRF(MYUSER)… USROPT(*HLPFULL *PRTMSG)
*CLKWD – Show CL keywords
F11 is a toggle switch to see choices or CL Keywords. *CLKWD simply changes the display you see first; choices or keywords.
When Prompting a Control Language command with F4=Prompt, we first see a textual description of the choices you can enter for the parameter on the right side of the parameter entry area. If we press F11=Keywords, we will see the CL keyword names to the left of the parameter entry area.
If we assign the user option *CLKWD to a user profile, these displays are reversed. In other words, you will first be prompted with the CL Keywords, and will see the choices after pressing F11=Choices.
*EXPERT – Use expert mode on certain displays
*EXPERT mode removes the instructions on some operational screens. It is similar to setting the *ADVANCED assistance level on screens that support that level.
*ROLLKEY – Change page up/page down
If you set the *ROLLKEY option for a user, the functions of page up and page down are reversed.
*NOSTSMSG or *STSMSG – *Status message display
I guess some users get real confused when they see those status messages blinking at them from line 24 of the display. It happens a lot during Query operations, and will also show up in custom code where the programmer is sending *status messages to keep the user informed.
But as the programmer, you may not want the user to know what the code is doing, so sometimes you want to hide your *status messages.
If *STSMSG is selected, the user will see status messages. If *NOSTSMSG is selected, the user will not see *status messages. If neither of these values is selected, the user will see *status messages.
Caveat: There are other avenues to control the display of *status messages: the system value QSTSMSG and the job attribute STSMSG.
*HLPFULL – Full screen help text
The i/OS has great HELP facilities. Cursor-sensitive HELP text is available on all IBM displays, and IBM and 3rd party vendors have provided great tools to easily build HELP text for your own application screens.
When you use the F1=HELP key, you typically get a limited help text window, which you can then scroll through to view the entire help text.
The *HLPFULL user option changes that windowed help text to cover the entire screen instead of a fraction of the screen. So *HLPFULL means full screen help text. I like this user option.
*PRTMSG – Message on printing action
By turning on *PRTMSG for a user, they receive an interrupting message telling them when their report is done printing.
Thursday, September 4, 2008
How your credit card works:
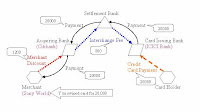
Priya: I want to buy a Sony digital camera costing Rs.20,000, but I don’t have any cash right now.
Raj: Why don’t you use your ICICI Bank credit card? Never heard them say? Hum Hain Na??
Priya: I am quite skeptic about using these cards. I pay using the card; get a bill after 30 days and pay after another 20 days. This is a maximum of 50 days interest free loan. Why does any bank do it?
If I borrow Rs.20,000 on personal loan at 11%.
Interest to be paid for 50 days = Rs. 20,000 * 11% * (50/365) = Rs. 301.40.
Here the bank is giving me a loan without interest when I use the credit card. Something is wrong somewhere!
Raj: Well? let me tell you how it works when you use your card to pay for the camera.
You present your ICICI Bank credit card a VISA card.
Sony World swipes your card on a machine provided by Citibank. Let’s call Citibank the acquirer bank and the process of Sony World swiping the card on that machine requesting authorization.
Citibank communicates with the card issuer.ICICI Bank through VISA Network to check if the card is valid and has the required credit limit.
ICICI Bank reviews and approves / declines which is communicated back to Sony World.
You sign a receipt called Sales Draft given by Citibank. This is the obligation on your part to pay the money to ICICI Bank. Data on this receipt can be captured electronically and transmitted.
At the end of day or at the end of some period Sony World chooses:
Sony World submits the receipt you signed to Citibank who pays Sony World the money. Sony World pays Citibank a fee called Merchant Discount. Let us say this is 6% of the sale value = 6% * 20,000 = Rs. 1200
Citibank sends the receipt electronically to a Visa data center which in turn sends it to ICICI Bank.
ICICI Bank transfers the money to a settlement bank which in turn transfers the funds to Citibank.
Citibank pays ICICI Bank an Interchange Fee of 4% of the sale value = 4% * 20,000 = Rs. 800
20 to 50 days later ICICI Bank gets the money from you? And you don’t pay the interest!!
Priya: Interesting! So Sony World pays more than the interest that I should have paid for the loan that I take. I, as a cardholder have the following benefits
1. Convenience of not having to carry cash.
2. Credit availability? Free of interest.
However what benefits does Sony World get for paying so much money? Isn’t it more profitable for them to take cash? They can save as much as Rs.1200.
Raj: Certainly. Some retail outlets offer you discounts if you pay by cash, don’t they?
However when you don’t count the money that you are spending, you tend to buy more! Cards encourage this? Called impulse purchase.
If you did not have access to credit, you would not have bought the camera this month? Or may be not any time soon either. By accepting cards, the merchant is actually extending you credit at the risk of the card issuer. He pays money to the banks to carry that risk.
Priya: So ICICI Bank uses this money to pay back to us when they announce 5% cash back. They insist that the Sales draft that I sign at the retailer should also be from ICICI Bank. This means they are saving on the Interchange Fee and also pay me a part of the Merchant Discount that they get.
Raj: Exactly! If you have noticed, ICICI Bank gives you the cash back in the next credit card statement. They keep the cash back money for a maximum of 60 days before passing on a part to you. This accrues them interest too.
Say if ICICI Bank earns an interest of 6% per annum for the cash they carry they get Rs.1000 * 6% * (60/365) = Rs. 10
That is not huge, but money nevertheless. And when you consider that almost everyone in this city shops with a credit card these days, it is a big sum.
Priya: And that also explains why banks tie up with petrol pumps like ICICI Bank has tied up with HPCL and I could re-fuel there without having to pay the fuel surcharge of 2.5%. The card issuer and the acquiring bank is the same and that saves interchange fees.
Raj: Good! You seem to have figured out how it all works! Let me summarize:
Priya: Toh ab shopping chalein?? Lets not miss the Shopping at the time of our celebration!
Wednesday, September 3, 2008
Executing Commands with system() function in RPG:
To call the system() function, you simply pass it a pointer to the command string. Here's the suggested prototype (along with some necessary H-specs):
/If Defined(*Crtbndrpg)
H Dftactgrp(*No)
/Endif
H Bnddir('QC2LE')
// ------------------------------------------------------- Prototypes
D GoCmd PR 10I 0 Extproc('system')
D CmdString * Value
D Options(*String)
The command string may be a variable, literal, named constant, or an expression. The following example shows a typical use:
/If Defined(*Crtbndrpg)
H Dftactgrp(*No)
/Endif
H Bnddir('QC2LE')
// ------------------------------------------------------- Prototypes
D GoCmd PR 10I 0 Extproc('system')
D CmdString * Value
D Options(*String)
D NullString
C -1
D Success C 0
D Returncode S 10I 0
D User S 10 Inz(*User) Varying
/Free
Returncode = Gocmd('WRKSPLF SELECT(' + User + ') OUTPUT(*PRINT)');
Select;
When Returncode = Success; // Command was successful
...
When Returncode = NullString; // Command string was null
...
Other;
// Command failed
...
Endsl;
/End-free
The return code will let you check for the success or failure of the system() function. The return code is zero if the command is successful, or 1 if the command fails. If you pass a null pointer to a string, system() returns -1, and the command processor is not called.
If the system() function fails (i.e., return code is 1), it sets a global variable _EXCP_MSGID with the CPF message ID. You can import this variable into your program to check for specific errors, as the
following example shows:
/If Defined(*Crtbndrpg)
H Dftactgrp(*No)
/Endif
H Bnddir('QC2LE')
// ------------------------------------------------------- Prototypes
D GoCmd PR 10I 0 Extproc('system')
D CmdString * Value
D Options(*String)
D NullString C -1
D Success C
0
D ObjectNotFound C 'CPF3142'
D ObjectInUse C 'CPF3156'
D Errmsgid S 7 Import('_EXCP_MSGID')
D Returncode S 10I 0
/Free
Returncode = Gocmd('DLTF MYLIB/MYFILE');
Select;
When Returncode = Success; // Command was successful
...
When Returncode = NullString; // Command string was null
...
When Errmsgid = ObjectNotFound; // CPF3142
...
When ErrMsgid = ObjectInUse; // CPF3156
...
Other; // Some other error
...
Endsl;
/End-free
To use the system() function, you must refer to binding directory QC2LE when compiling and/or binding the program. The above examples name QC2LE in the H-specs.
Handle errors in RPG like CL:
Example:
Declare an array like Arr with DIM(2) Declare 3 variables A, B and C with length 2,0.
The below code shows, how to monitor the runtime errors. The initial value of A and C is 0, initiate value of B is 11.
MONITOR
B DIV A
Arr(B) Dsply
ON-ERROR 0102
'Div by 0' Dsply
ON-ERROR 0121
'Index Err' Dsply
ON-ERROR
'Error' Dsply
ENDMON
Similar way specific errors can be captured and handled accordingly in RPG.
Monday, September 1, 2008
Vacation and Out of Office:
when you save the document Lotus Notes automatically asks you if you want to set up the Out of Office feature.
If yes is pressed, then it will lead to the out of office set up and makes it easier.
Sunday, August 31, 2008
OCT – Operation Cost Target:
Tuesday, August 26, 2008
Calendar Coloring in Lotus Notes:
In Preferenes -> Calendar & To Do -> Colors, there is a option to set colors for the New meetings and Cancelled meetings.
Here is an example where we invite a person to a meeting.
He has not yet accepted the calendar invite that is in his in-box, but Notes 8 now displays the unprocessed meeting on his calendar anyway.
After he accepts, it is displayed as we would expect.
Then as the chairperson we have to unfortunately cancel the meeting. The person has not had the time to open the cancellation notice in his email, but Notes 8 automatically changes the way the meeting is displayed on his calendar, visually informing him that the meeting has been cancelled.
Monday, August 25, 2008
Quick method to find the name of the Calling Program:
D GetCaller PR Extpgm('QWVRCSTK')
D 2000
D 10I 0
D 8 CONST
D 56
D 8 CONST
D 15
D Var DS 2000
D BytAvl 10I 0
D BytRtn 10I 0
D Entries 10I 0
D Offset 10I 0
D EntryCount 10I 0
D VarLen S 10I 0 Inz(%size(Var))
D ApiErr S 15
D JobIdInf DS
D JIDQName 26 Inz('*')
D JIDIntID 16
D JIDRes3 2 Inz(*loval)
D JIDThreadInd 10I 0 Inz(1)
D JIDThread 8 Inz(*loval)
D Entry DS 256
D EntryLen 10I 0
D PgmNam 10 Overlay(Entry:25)
D PgmLib 10 Overlay(Entry:35)
D
C CallP GetCaller(Var:VarLen:'CSTK0100':JobIdInf
C :'JIDF0100':ApiErr)
C Do EntryCount
C Eval Entry = %subst(Var:Offset + 1)
C Eval Offset = Offset + EntryLen
C Enddo
C Eval *InLR = *on
Sunday, August 24, 2008
Tips for faster Query Access:
• Code a Set Option AlwCpyDta = *Optimize SQL statement (or the AlwCpyDta(*Optimize) parameter on the appropriate CL command). This lets the optimizer choose whether to create a new index or use a sort for a temporary copy of the data.
• Note that AlwCpyDta=*Yes actually means "use a copy only when it's required to perform the query." This allows the optimizer less latitude than the *Optimize option provides.
• Code a Set Option AlwBlk = *AllRead SQL statement (or the AlwBlk(*AllRead) parameter on the appropriate CL command). This maximizes system blocking when possible.
• Use a CL OvrDbF (Override with Database File) command with the SeqOnly(*Yes, mm) and/or the NbrRcds(nn) parameter(s) to specify system blocking for batch sequential Fetch's.
Use multi-row fetches to read a set of records with each Fetch statement.
Friday, August 22, 2008
V5R3 Enhancement in SQL:
create table qtemp/Plants (ID char(4),Name char(12))
To create rows (records) for two factories, you could use two insert commands.
insert into qtemp/plants values('1492', 'Lost Angeles')
insert into qtemp/plants values('2001', 'New Yolk')
In V5R3, IBM enhanced the VALUES form of INSERT to permit you to insert more than one row at a time. The following INSERT command inserts two rows.
insert into qtemp/plants values ('1492', 'Lost Angeles'), ('2001', 'New Yolk')
Each row's values are enclosed in parentheses and separated from other rows with commas.
This is not an IBM-only feature. Other SQL platforms support it as well.
Thursday, August 21, 2008
Right Justify Character data using SQL:
INSERT INTO TARGET_TABLE
SITE_CODE_RIGHT_JUSTIFED
SELECT
SUBSTR(' ', 1, 12 -
LENGTH( TRIM( CHAR_COLUMN_NAME)))
|| TRIM( CHAR_COLUMN_NAME )
FROM TABLE
FROM SOURCE_DATA