How to Verify your JD Edwards World Release Level
From any menu, type 97 on the command line.
Under the column labeled Release Level, find the highest letter/number combination. For example A8.1.
Tuesday, September 30, 2008
Monday, September 29, 2008
Category Killer:
Definition: A large retail chain store that is dominant in its product category. This type of store generally offers an extensive selection of merchandise at prices so low that smaller stores cannot compete.
Also Known As: Big Box Store
Examples: Best Buy is an example of an electronics category killer.
Also Known As: Big Box Store
Examples: Best Buy is an example of an electronics category killer.
Sunday, September 28, 2008
How to stop Procrastinating:
• Recognize that procrastination stems from habit. New habits will be needed, and these take time and commitment to develop.
• Harold Taylor defines procrastination as the intentional and habitual postponement of an important task that should be done now.
• Understand the cause for procrastination, then develop strategies to fix it.
• Recognize the difference between an appropriate decision to delay, and an irrational postponement without justification.
• Fix procrastination by working on a) tasks and b) your environment:
TASK STRATEGIES
Unpleasant tasks
• Unpleasant tasks rarely turn out to be as bad as you think.
• Complete these tasks first. Schedule them for early in the day. Give yourself a reward for doing them.
Complex Projects
• Something looms ahead of you: starting a small business, getting a job, preparing the annual budget. The job is too big or will take too long to do now, so you put it off.
• Break large jobs into smaller, more manageable tasks. Plan and complete a start-up task, no matter how small.
Indecision
• People delay because they can't make up their minds.
• Determine a time for making a decision and the criteria for making it. Share your deadline with someone else.
Fear of failure (lack of self confidence)
• People don't want to face the consequences of failure, so they delay. (Some people suffer from fear of success too!)
• Develop a clear mental picture of the completed task and how you will feel at that time. Maintain a focus on the end result, not just the process. Remind yourself how good you'll feel when you're finished.
Lack of interest
• You are tired or lazy. You're just not very interested in the task.
• Reward yourself for accomplishments. Go out for special lunches when major projects are completed. If you don't earn the reward, don't take it.
• Schedule the task for when you will be at your peak.
Perfectionism
• People delay because they want to get the project perfect.
• Set deadlines for yourself. Tell other people your deadlines and encourage them to check up on you.
• Maintain your high standards, but recognize that sometimes 80% for you may well be 100% for someone else. Don't spend hours conducting a detailed cost breakdown when a rough estimate would suffice.
Hostility towards a boss
• People delay because they don't like the person who assigned the task.
• Review with your boss what exactly is needed. Clarify the expectations.
• Make a game out of unpleasant tasks. Give yourself points, or do a running commentary on yourself as you do the task.
Distraction, lack of focus
• Sometimes losing concentration causes delays.
• Create a to-do list with priorities.
• Block your time for projects.
• As you get distracted from a work project, make a rule that you are not allowed to move out of your chair, make a call, surf the net, pick up a book etc. until you return to your task.
• Complete something. Make a very small task for yourself and finish it. Very small. Then, make another one.
ENVIRONMENT STRATEGIES
• Tailor your environment for work. Close your door, clean up the clutter on your desk.
• Remove distractions such as water coolers, snacks, in-boxes, coffee machines and magazine racks.
• If you work at home, treat your office as an office. Don't go out to lunch before lunchtime or watch television before the end of the day.
• Tell your family that you are not to be disturbed in your home office.
• Harold Taylor defines procrastination as the intentional and habitual postponement of an important task that should be done now.
• Understand the cause for procrastination, then develop strategies to fix it.
• Recognize the difference between an appropriate decision to delay, and an irrational postponement without justification.
• Fix procrastination by working on a) tasks and b) your environment:
TASK STRATEGIES
Unpleasant tasks
• Unpleasant tasks rarely turn out to be as bad as you think.
• Complete these tasks first. Schedule them for early in the day. Give yourself a reward for doing them.
Complex Projects
• Something looms ahead of you: starting a small business, getting a job, preparing the annual budget. The job is too big or will take too long to do now, so you put it off.
• Break large jobs into smaller, more manageable tasks. Plan and complete a start-up task, no matter how small.
Indecision
• People delay because they can't make up their minds.
• Determine a time for making a decision and the criteria for making it. Share your deadline with someone else.
Fear of failure (lack of self confidence)
• People don't want to face the consequences of failure, so they delay. (Some people suffer from fear of success too!)
• Develop a clear mental picture of the completed task and how you will feel at that time. Maintain a focus on the end result, not just the process. Remind yourself how good you'll feel when you're finished.
Lack of interest
• You are tired or lazy. You're just not very interested in the task.
• Reward yourself for accomplishments. Go out for special lunches when major projects are completed. If you don't earn the reward, don't take it.
• Schedule the task for when you will be at your peak.
Perfectionism
• People delay because they want to get the project perfect.
• Set deadlines for yourself. Tell other people your deadlines and encourage them to check up on you.
• Maintain your high standards, but recognize that sometimes 80% for you may well be 100% for someone else. Don't spend hours conducting a detailed cost breakdown when a rough estimate would suffice.
Hostility towards a boss
• People delay because they don't like the person who assigned the task.
• Review with your boss what exactly is needed. Clarify the expectations.
• Make a game out of unpleasant tasks. Give yourself points, or do a running commentary on yourself as you do the task.
Distraction, lack of focus
• Sometimes losing concentration causes delays.
• Create a to-do list with priorities.
• Block your time for projects.
• As you get distracted from a work project, make a rule that you are not allowed to move out of your chair, make a call, surf the net, pick up a book etc. until you return to your task.
• Complete something. Make a very small task for yourself and finish it. Very small. Then, make another one.
ENVIRONMENT STRATEGIES
• Tailor your environment for work. Close your door, clean up the clutter on your desk.
• Remove distractions such as water coolers, snacks, in-boxes, coffee machines and magazine racks.
• If you work at home, treat your office as an office. Don't go out to lunch before lunchtime or watch television before the end of the day.
• Tell your family that you are not to be disturbed in your home office.
Thursday, September 25, 2008
SQL Case Expression:
An SQL case expression offers a simple way to add conditional evaluation to an SQL statement. It can often simplify what would otherwise be a difficult or even impossible task.
Use:
Multiple updates based on multiple conditions, in one pass could be done by SQL case expressions:
E.g.:
The following two SQL statements can be combined into one. The single statement may run faster, especially against a large file, since it makes only one pass.
Update filename set field1 = 'Y1' where field1 = 'X1'
Update filename set field2 = 'Y2' where field2 = 'X2'
Single statement:
Update filename set
field1 = CASE
When field1 = 'X1' then 'Y1'
Else field1
END,
field2 = CASE
When field2 = 'X2' then 'Y2'
Else field2
END
Where field1 = 'X1' or field2 = 'X2'
Use:
Multiple updates based on multiple conditions, in one pass could be done by SQL case expressions:
E.g.:
The following two SQL statements can be combined into one. The single statement may run faster, especially against a large file, since it makes only one pass.
Update filename set field1 = 'Y1' where field1 = 'X1'
Update filename set field2 = 'Y2' where field2 = 'X2'
Single statement:
Update filename set
field1 = CASE
When field1 = 'X1' then 'Y1'
Else field1
END,
field2 = CASE
When field2 = 'X2' then 'Y2'
Else field2
END
Where field1 = 'X1' or field2 = 'X2'
Wednesday, September 24, 2008
Conflict Resolution:
In many cases, conflict in the workplace just seems to be a fact of life. We've all seen situations where different people with different goals and needs have come into conflict.
The fact that conflict exists, however, is not necessarily a bad thing: As long as it is resolved effectively, it can lead to personal and professional growth.
In many cases, effective conflict resolution skills can make the difference between positive and negative outcomes.
Negative Effects:
However, if conflict is not handled effectively, the results can be damaging. Conflicting goals can quickly turn into,
• Personal dislike.
• Teamwork breaks down.
• Talent is wastage of people.
Different Styles for different situations.
Once you understand the different styles, you can use them to think about the most appropriate approach (or mixture of approaches) for the situation you're in. You can also think about your own instinctive approach, and learn how you need to change this if necessary.
Competitive: People who tend towards a competitive style take a firm stand, and know what they want. They usually operate from a position of power, drawn from things like position, rank, expertise, or persuasive ability. This style can be useful when there is an emergency and a decision needs to be make fast; when the decision is unpopular; or when defending against someone who is trying to exploit the situation selfishly. However it can leave people feeling bruised, unsatisfied and resentful when used in less urgent situations.
Collaborative: People tending towards a collaborative style try to meet the needs of all people involved. These people can be highly assertive but unlike the competitor, they cooperate effectively and acknowledge that everyone is important. This style is useful when a you need to bring together a variety of viewpoints to get the best solution; when there have been previous conflicts in the group; or when the situation is too important for a simple trade-off.
Compromising: People who prefer a compromising style try to find a solution that will at least partially satisfy everyone. Everyone is expected to give up something, and the compromiser him- or herself also expects to relinquish something. Compromise is useful when the cost of conflict is higher than the cost of losing ground, when equal strength opponents are at a standstill and when there is a deadline looming.
Accommodating: This style indicates a willingness to meet the needs of others at the expense of the person’s own needs. The accommodator often knows when to give in to others, but can be persuaded to surrender a position even when it is not warranted. This person is not assertive but is highly cooperative. Accommodation is appropriate when the issues matter more to the other party, when peace is more valuable than winning, or when you want to be in a position to collect on this “favor” you gave. However people may not return favors, and overall this approach is unlikely to give the best outcomes.
Avoiding: People tending towards this style seek to evade the conflict entirely. This style is typified by delegating controversial decisions, accepting default decisions, and not wanting to hurt anyone’s feelings. It can be appropriate when victory is impossible, when the controversy is trivial, or when someone else is in a better position to solve the problem. However in many situations this is a weak and ineffective approach to take.
Tips for better conflict Resolution:
• Make sure that good relationships are the first priority: As far as possible, make sure that you treat the other calmly and that you try to build mutual respect. Do your best to be courteous to one-another and remain constructive under pressure;
• Keep people and problems separate: Recognize that in many cases the other person is not just "being difficult" – real and valid differences can lie behind conflictive positions. By separating the problem from the person, real issues can be debated without damaging working relationships;
• Pay attention to the interests that are being presented: By listening carefully you'll most-likely understand why the person is adopting his or her position;
• Listen first; talk second: To solve a problem effectively you have to understand where the other person is coming from before defending your own position;
• Set out the “Facts”: Agree and establish the objective, observable elements that will have an impact on the decision; and
• Explore options together: Be open to the idea that a third position may exist, and that you can get to this idea jointly.
The fact that conflict exists, however, is not necessarily a bad thing: As long as it is resolved effectively, it can lead to personal and professional growth.
In many cases, effective conflict resolution skills can make the difference between positive and negative outcomes.
Negative Effects:
However, if conflict is not handled effectively, the results can be damaging. Conflicting goals can quickly turn into,
• Personal dislike.
• Teamwork breaks down.
• Talent is wastage of people.
Different Styles for different situations.
Once you understand the different styles, you can use them to think about the most appropriate approach (or mixture of approaches) for the situation you're in. You can also think about your own instinctive approach, and learn how you need to change this if necessary.
Competitive: People who tend towards a competitive style take a firm stand, and know what they want. They usually operate from a position of power, drawn from things like position, rank, expertise, or persuasive ability. This style can be useful when there is an emergency and a decision needs to be make fast; when the decision is unpopular; or when defending against someone who is trying to exploit the situation selfishly. However it can leave people feeling bruised, unsatisfied and resentful when used in less urgent situations.
Collaborative: People tending towards a collaborative style try to meet the needs of all people involved. These people can be highly assertive but unlike the competitor, they cooperate effectively and acknowledge that everyone is important. This style is useful when a you need to bring together a variety of viewpoints to get the best solution; when there have been previous conflicts in the group; or when the situation is too important for a simple trade-off.
Compromising: People who prefer a compromising style try to find a solution that will at least partially satisfy everyone. Everyone is expected to give up something, and the compromiser him- or herself also expects to relinquish something. Compromise is useful when the cost of conflict is higher than the cost of losing ground, when equal strength opponents are at a standstill and when there is a deadline looming.
Accommodating: This style indicates a willingness to meet the needs of others at the expense of the person’s own needs. The accommodator often knows when to give in to others, but can be persuaded to surrender a position even when it is not warranted. This person is not assertive but is highly cooperative. Accommodation is appropriate when the issues matter more to the other party, when peace is more valuable than winning, or when you want to be in a position to collect on this “favor” you gave. However people may not return favors, and overall this approach is unlikely to give the best outcomes.
Avoiding: People tending towards this style seek to evade the conflict entirely. This style is typified by delegating controversial decisions, accepting default decisions, and not wanting to hurt anyone’s feelings. It can be appropriate when victory is impossible, when the controversy is trivial, or when someone else is in a better position to solve the problem. However in many situations this is a weak and ineffective approach to take.
Tips for better conflict Resolution:
• Make sure that good relationships are the first priority: As far as possible, make sure that you treat the other calmly and that you try to build mutual respect. Do your best to be courteous to one-another and remain constructive under pressure;
• Keep people and problems separate: Recognize that in many cases the other person is not just "being difficult" – real and valid differences can lie behind conflictive positions. By separating the problem from the person, real issues can be debated without damaging working relationships;
• Pay attention to the interests that are being presented: By listening carefully you'll most-likely understand why the person is adopting his or her position;
• Listen first; talk second: To solve a problem effectively you have to understand where the other person is coming from before defending your own position;
• Set out the “Facts”: Agree and establish the objective, observable elements that will have an impact on the decision; and
• Explore options together: Be open to the idea that a third position may exist, and that you can get to this idea jointly.
Tuesday, September 23, 2008
Delivery Option in Lotus Notes Mail:
When you open new Memo you can get this option on the top which holds various options which will be triggered when you send a mail. These options are –
Setting the importance of the mail, Mood stamps
Setting various Delivery reports.
Auto spell check, Return Receipt & Encryption.
Setting Expiration and Archiving stamp for the recipient.
Another handy option we have in Advanced Tab which controls the Reply option of a mail. By putting a Person/Group name in Delivery Option the recipient will see whom he has to Reply and it automatically Replies to that person when he selects “Reply” option.
To know whether a mail has RR, go to document property and check for a field named “Return Receipt”. If the value of the field is “1” that means it has Return Receipt option enabled. Also to stop a Return Receipt, immediately after opening the mail you need to go to Outbox view just under Inbox option and delete that mail.
Another feature is “Return receipt” which let you know when the recipient has Opened/Marked a mail as “Unread”.
Another very important feature is “Prevent Copying”. When you do not want the recipient to copy your mail or Forward to someone you can select this option.
Setting the importance of the mail, Mood stamps
Setting various Delivery reports.
Auto spell check, Return Receipt & Encryption.
Setting Expiration and Archiving stamp for the recipient.
Another handy option we have in Advanced Tab which controls the Reply option of a mail. By putting a Person/Group name in Delivery Option the recipient will see whom he has to Reply and it automatically Replies to that person when he selects “Reply” option.
To know whether a mail has RR, go to document property and check for a field named “Return Receipt”. If the value of the field is “1” that means it has Return Receipt option enabled. Also to stop a Return Receipt, immediately after opening the mail you need to go to Outbox view just under Inbox option and delete that mail.
Another feature is “Return receipt” which let you know when the recipient has Opened/Marked a mail as “Unread”.
Another very important feature is “Prevent Copying”. When you do not want the recipient to copy your mail or Forward to someone you can select this option.
Monday, September 22, 2008
Replace the Value of the field in a particular position in SQL:
A particular position or a particular value in a string can be replaced with a new value in SQL. REPLACE function does the job.
Syntax:
REPLACE (string_expression1, string_expression2, string_expression3)
string_expression1
Is the string expression to be searched. string_expression1 can be of a character or binary data type.
string_expression2
Is the substring to be found. string_expression2 can be of a character or binary data type.
string_expression3
Is the replacement string. string_expression3 can be of a character or binary data type.
Example:
UPDATE kgipkemp set kmfld1 = REPLACE(kmfld1,substr(kmfld1,21,6), '080901' )
Syntax:
REPLACE (string_expression1, string_expression2, string_expression3)
string_expression1
Is the string expression to be searched. string_expression1 can be of a character or binary data type.
string_expression2
Is the substring to be found. string_expression2 can be of a character or binary data type.
string_expression3
Is the replacement string. string_expression3 can be of a character or binary data type.
Example:
UPDATE kgipkemp set kmfld1 = REPLACE(kmfld1,substr(kmfld1,21,6), '080901' )
Sunday, September 21, 2008
Display Status Message in Reverse Image:
To display status messages in reverse image, define two single-character fields to hold the hex code for display attributes: one to contain the reverse-image attribute byte and one to contain the normal attribute byte. Then, concatenate these fields with your message field, as the following partial program illustrates.
DCL VAR(&REVERSE) TYPE(*CHAR) LEN(1) VALUE(X'21')
DCL VAR(&NORMAL) TYPE(*CHAR) LEN(1) VALUE(X'20')
SNDPGMMSG MSGID(CPF9898) MSGF(QCPFMSG) +
MSGDTA(&REVERSE *CAT &MSG *CAT &NORMAL) +
TOPGMQ(*EXT) MSGTYPE(*STATUS)
DCL VAR(&REVERSE) TYPE(*CHAR) LEN(1) VALUE(X'21')
DCL VAR(&NORMAL) TYPE(*CHAR) LEN(1) VALUE(X'20')
SNDPGMMSG MSGID(CPF9898) MSGF(QCPFMSG) +
MSGDTA(&REVERSE *CAT &MSG *CAT &NORMAL) +
TOPGMQ(*EXT) MSGTYPE(*STATUS)
Thursday, September 18, 2008
BIOS:
This is the Basic Input/Output System and is installed on the computer's motherboard. It controls the most basic operations and is responsible for starting your computer up and initializing the hardware. It is data that is usually held in a ROM chip, which can be updated by "flashing". BIOS upgrades may correct errors, support new CPUs, support new hardware, etc.
The primary function of the BIOS is to identify and initialize system component hardware (such as the video display card, hard disk, and floppy disk) and some other hardware devices. This is to prepare the machine into a known low capability state, so other software programs stored on various media can be loaded, executed, and given control of the PC. This process is known as booting, or booting up, which is short for bootstrapping.
Major BIOS vendors include American Megatrends (AMI), General Software, Insyde Software, and Phoenix Technologies.
The primary function of the BIOS is to identify and initialize system component hardware (such as the video display card, hard disk, and floppy disk) and some other hardware devices. This is to prepare the machine into a known low capability state, so other software programs stored on various media can be loaded, executed, and given control of the PC. This process is known as booting, or booting up, which is short for bootstrapping.
Major BIOS vendors include American Megatrends (AMI), General Software, Insyde Software, and Phoenix Technologies.
Comp Sales:
Definition: A measurement of productivity in revenue used to compare sales of retail stores that have been open for a year or more. Historical sales data allows retailers to compare this year's sales in their store to the same period last year.
Also Known As: Same-Store Sales, Comparable Store Sales, Comp-Store
Examples: Best Buy showed an impressive comp-store sales growth of 5.9% last quarter which was fueled by strength in flat-panel TVs, video gaming hardware and notebook computers.
Also Known As: Same-Store Sales, Comparable Store Sales, Comp-Store
Examples: Best Buy showed an impressive comp-store sales growth of 5.9% last quarter which was fueled by strength in flat-panel TVs, video gaming hardware and notebook computers.
Wednesday, September 17, 2008
RSS Feed:
RSS (Rich Site Summary) is a format for delivering regularly changing web content. Many news-related sites, weblogs and other online publishers syndicate their content as an RSS Feed to whoever wants it.
RSS solves a problem for people who regularly use the web. It allows you to easily stay informed by retrieving the latest content from the sites you are interested in. You save time by not needing to visit each site individually. You ensure your privacy, by not needing to join each site's email newsletter.
RSS feeds can be read using software called an "RSS reader," "feed reader," or an "aggregator," which can be web-based or desktop-based.
The user subscribes to a feed by entering the feed's link into the reader or by clicking an RSS icon in a browser that initiates the subscription process. The RSS reader checks the user's subscribed feeds regularly for new work, downloads any updates that it finds, and provides a user interface to monitor and read the feeds.
RSS solves a problem for people who regularly use the web. It allows you to easily stay informed by retrieving the latest content from the sites you are interested in. You save time by not needing to visit each site individually. You ensure your privacy, by not needing to join each site's email newsletter.
RSS feeds can be read using software called an "RSS reader," "feed reader," or an "aggregator," which can be web-based or desktop-based.
The user subscribes to a feed by entering the feed's link into the reader or by clicking an RSS icon in a browser that initiates the subscription process. The RSS reader checks the user's subscribed feeds regularly for new work, downloads any updates that it finds, and provides a user interface to monitor and read the feeds.
Monday, September 15, 2008
Find Data in a Multi-Member file:
Ever have to look through a large multimember file for a particular record? It can be a time consuming task.
Key in FNDSTRPDM + F4. Options are self-explanatory.
Option member allow user to key in "*ALL" and will search through all members for the strings keyed.
Allows user to display, print, and edit records when string is found.
Key in FNDSTRPDM + F4. Options are self-explanatory.
Option member allow user to key in "*ALL" and will search through all members for the strings keyed.
Allows user to display, print, and edit records when string is found.
Sunday, September 14, 2008
Size Matters:
Before you start the process of replicating your Lotus Notes mail file to your computer (local), you should check to make sure you have enough free space on your hard drive. To check the size of your mail (actually, of any Notes database) you use the Properties Box. You can open the Properties Box by either pressing ALT+ENTER on your keyboard, choosing File - Database - Properties from the menus, or clicking the toolbar icon.
With the Properties Box open, switch to the second tab "i" for Information. There you can see the size of your mail file.
With the Properties Box open, switch to the second tab "i" for Information. There you can see the size of your mail file.
Thursday, September 11, 2008
Break-Even Point:
The point in business where the sales equal the expenses. There is no profit and no loss.
Formula:
Break-Even Point ($) = Fixed Costs ÷ Gross Margin Percentage
Also Known As: Breakeven Analysis
Examples: Our retail store buys widgets for $15 each, marks them up and sells them for $30. Our monthly expenses (fixed costs) are $10,000. This means our breakeven point would be $20,000 or 667 units.
$10,000 ÷ (15/30) = $20,000
$20,000 ÷ $30 = 667
Formula:
Break-Even Point ($) = Fixed Costs ÷ Gross Margin Percentage
Also Known As: Breakeven Analysis
Examples: Our retail store buys widgets for $15 each, marks them up and sells them for $30. Our monthly expenses (fixed costs) are $10,000. This means our breakeven point would be $20,000 or 667 units.
$10,000 ÷ (15/30) = $20,000
$20,000 ÷ $30 = 667
Wednesday, September 10, 2008
Nominal Group Technique:
The nominal group technique is a decision making method for use among groups of many sizes, who want to make their decision quickly, as by a vote, but want everyone's opinions taken into account (as opposed to traditional voting, where only the largest group is considered) . The method of tallying is the difference. First, every member of the group gives their view of the solution, with a short explanation. Then, duplicate solutions are eliminated from the list of all solutions, and the members proceed to rank the solutions, 1st, 2nd, 3rd, 4th, and so on. The numbers each solution receives are totaled, and the solution with the lowest (i.e. most favored) total ranking is selected as the final decision. There are variations on how this technique is used. For example, it can identify strengths versus areas in need of development, rather than be used as a decision-making voting alternative. Also, options do not always have to be ranked, but may be evaluated more subjectively.
When to use this technique:
• When some group members are much more vocal than others.
• When some group members think better in silence.
• When there is concern about some members not participating.
• When the group does not easily generate quantities of ideas.
• When all or some group members are new to the team.
• When the issue is controversial or there is heated conflict.
As with any technique, there are advantages and disadvantages. NGT is no exception. One major advantage of NGT is that it avoids two problems caused by group interaction. First, some members are reluctant to suggest ideas because they are concerned about being criticized. Second, some members are reluctant to create conflict in groups. (Many people want to maintain a pleasant climate.) NGT overcomes these problems. NGT has the clear advantage of minimizing differences and ensuring relatively equal participation. It may also, in many cases be a time-saving technique. Other advantages include producing a large number of ideas and providing a sense of closure that is often not found in less-structured group methods.
Major disadvantage of NGT is that the method lacks flexibility by only being able to deal with one problem at a time. Also, there must be a certain amount of conformity on the part of the members involved in NGT. Everyone must feel comfortable with the amount of structure involved. Another disadvantage is the amount of time needed to prepare for the activity. There is no spontaneity involved with this method. Facilities must be arranged and carefully planned. Opinions may not converge in the voting process, cross-fertilization, of ideas may be constrained, and the process may appear to be too mechanical.
When to use this technique:
• When some group members are much more vocal than others.
• When some group members think better in silence.
• When there is concern about some members not participating.
• When the group does not easily generate quantities of ideas.
• When all or some group members are new to the team.
• When the issue is controversial or there is heated conflict.
As with any technique, there are advantages and disadvantages. NGT is no exception. One major advantage of NGT is that it avoids two problems caused by group interaction. First, some members are reluctant to suggest ideas because they are concerned about being criticized. Second, some members are reluctant to create conflict in groups. (Many people want to maintain a pleasant climate.) NGT overcomes these problems. NGT has the clear advantage of minimizing differences and ensuring relatively equal participation. It may also, in many cases be a time-saving technique. Other advantages include producing a large number of ideas and providing a sense of closure that is often not found in less-structured group methods.
Major disadvantage of NGT is that the method lacks flexibility by only being able to deal with one problem at a time. Also, there must be a certain amount of conformity on the part of the members involved in NGT. Everyone must feel comfortable with the amount of structure involved. Another disadvantage is the amount of time needed to prepare for the activity. There is no spontaneity involved with this method. Facilities must be arranged and carefully planned. Opinions may not converge in the voting process, cross-fertilization, of ideas may be constrained, and the process may appear to be too mechanical.
Tuesday, September 9, 2008
Use SQL to remove extra spaces:
The REPLACE function can be used to remove extra spaces within a character string. IBM added the REPLACE function to SQL in V5R3.
Run the following query to see what would happen.
select name,
replace(replace(replace(name,' ','<>'),'><',''),'<>',' ')
from qtemp/mydata
This is the output:
NAME REPLACE
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
So how does it work? The innermost REPLACE changes all blanks to a less-than greater-than pair. So, if there are three spaces between Joe and Smith, the innermost REPLACE returns Joe<><><>Smith.
The middle REPLACE changes all greater-than less-than pairs to the empty string, which removes them. Joe<><><>Smith becomes Joe<>Smith.
The outer REPLACE changes all less-than greater-than pairs to a single blank. Joe<>Smith becomes Joe Smith.
You do not have to use the less-than and greater-than symbols. Any two characters that are not used in the field will work.
Run the following query to see what would happen.
select name,
replace(replace(replace(name,' ','<>'),'><',''),'<>',' ')
from qtemp/mydata
This is the output:
NAME REPLACE
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
Joe Smith Joe Smith
So how does it work? The innermost REPLACE changes all blanks to a less-than greater-than pair. So, if there are three spaces between Joe and Smith, the innermost REPLACE returns Joe<><><>Smith.
The middle REPLACE changes all greater-than less-than pairs to the empty string, which removes them. Joe<><><>Smith becomes Joe<>Smith.
The outer REPLACE changes all less-than greater-than pairs to a single blank. Joe<>Smith becomes Joe Smith.
You do not have to use the less-than and greater-than symbols. Any two characters that are not used in the field will work.
Monday, September 8, 2008
How does a Firewall work:
A firewall is a set of related programs, located at a network gateway server that protects the resources of a private network from users from other networks. (The term also implies the security policy that is used with the programs.) An enterprise with an intranet that allows its workers access to the wider Internet installs a firewall to prevent outsiders from accessing its own private data resources and for controlling what outside resources its own users have access to.
Basically, a firewall, working closely with a router program, examines each network packet to determine whether to forward it toward its destination. A firewall also includes or works with a proxy server that makes network requests on behalf of workstation users. A firewall is often installed in a specially designated computer separate from the rest of the network so that no incoming request can get directly at private network resources.
There are a number of firewall screening methods. A simple one is to screen requests to make sure they come from acceptable (previously identified) domain name and Internet Protocol addresses. For mobile users, firewalls allow remote access in to the private network by the use of secure logon procedures and authentication certificates.
A number of companies make firewall products. Features include logging and reporting, automatic alarms at given thresholds of attack, and a graphical user interface for controlling the firewall.
Basically, a firewall, working closely with a router program, examines each network packet to determine whether to forward it toward its destination. A firewall also includes or works with a proxy server that makes network requests on behalf of workstation users. A firewall is often installed in a specially designated computer separate from the rest of the network so that no incoming request can get directly at private network resources.
There are a number of firewall screening methods. A simple one is to screen requests to make sure they come from acceptable (previously identified) domain name and Internet Protocol addresses. For mobile users, firewalls allow remote access in to the private network by the use of secure logon procedures and authentication certificates.
A number of companies make firewall products. Features include logging and reporting, automatic alarms at given thresholds of attack, and a graphical user interface for controlling the firewall.
Sunday, September 7, 2008
Unexplored User profile User Options:
When you create or change a user profile, there are many optional parameters for which you can specify a value. Since we normally just clone an existing user profile to make a new one, most of us never get around to examining all of those optional parameters.
When using the CRTUSRPRF, CHGUSRPRF, or CHGPRF command, one of the last parameters is User Options(USROPT).
The default value for USROPT is *NONE, so when we do not specify an alternate value, we get no special options for that user.
The alternate values we can specify include *CLKWD, *EXPERT, *ROLLKEY, *NOSTSMSG, *STSMSG, *HLPFULL, and *PRTMSG.
Here's an example of using the USROPT parameter.
CRTUSRPRF USRPRF(MYUSER)… USROPT(*HLPFULL *PRTMSG)
*CLKWD – Show CL keywords
F11 is a toggle switch to see choices or CL Keywords. *CLKWD simply changes the display you see first; choices or keywords.
When Prompting a Control Language command with F4=Prompt, we first see a textual description of the choices you can enter for the parameter on the right side of the parameter entry area. If we press F11=Keywords, we will see the CL keyword names to the left of the parameter entry area.
If we assign the user option *CLKWD to a user profile, these displays are reversed. In other words, you will first be prompted with the CL Keywords, and will see the choices after pressing F11=Choices.
*EXPERT – Use expert mode on certain displays
*EXPERT mode removes the instructions on some operational screens. It is similar to setting the *ADVANCED assistance level on screens that support that level.
*ROLLKEY – Change page up/page down
If you set the *ROLLKEY option for a user, the functions of page up and page down are reversed.
*NOSTSMSG or *STSMSG – *Status message display
I guess some users get real confused when they see those status messages blinking at them from line 24 of the display. It happens a lot during Query operations, and will also show up in custom code where the programmer is sending *status messages to keep the user informed.
But as the programmer, you may not want the user to know what the code is doing, so sometimes you want to hide your *status messages.
If *STSMSG is selected, the user will see status messages. If *NOSTSMSG is selected, the user will not see *status messages. If neither of these values is selected, the user will see *status messages.
Caveat: There are other avenues to control the display of *status messages: the system value QSTSMSG and the job attribute STSMSG.
*HLPFULL – Full screen help text
The i/OS has great HELP facilities. Cursor-sensitive HELP text is available on all IBM displays, and IBM and 3rd party vendors have provided great tools to easily build HELP text for your own application screens.
When you use the F1=HELP key, you typically get a limited help text window, which you can then scroll through to view the entire help text.
The *HLPFULL user option changes that windowed help text to cover the entire screen instead of a fraction of the screen. So *HLPFULL means full screen help text. I like this user option.
*PRTMSG – Message on printing action
By turning on *PRTMSG for a user, they receive an interrupting message telling them when their report is done printing.
When using the CRTUSRPRF, CHGUSRPRF, or CHGPRF command, one of the last parameters is User Options(USROPT).
The default value for USROPT is *NONE, so when we do not specify an alternate value, we get no special options for that user.
The alternate values we can specify include *CLKWD, *EXPERT, *ROLLKEY, *NOSTSMSG, *STSMSG, *HLPFULL, and *PRTMSG.
Here's an example of using the USROPT parameter.
CRTUSRPRF USRPRF(MYUSER)… USROPT(*HLPFULL *PRTMSG)
*CLKWD – Show CL keywords
F11 is a toggle switch to see choices or CL Keywords. *CLKWD simply changes the display you see first; choices or keywords.
When Prompting a Control Language command with F4=Prompt, we first see a textual description of the choices you can enter for the parameter on the right side of the parameter entry area. If we press F11=Keywords, we will see the CL keyword names to the left of the parameter entry area.
If we assign the user option *CLKWD to a user profile, these displays are reversed. In other words, you will first be prompted with the CL Keywords, and will see the choices after pressing F11=Choices.
*EXPERT – Use expert mode on certain displays
*EXPERT mode removes the instructions on some operational screens. It is similar to setting the *ADVANCED assistance level on screens that support that level.
*ROLLKEY – Change page up/page down
If you set the *ROLLKEY option for a user, the functions of page up and page down are reversed.
*NOSTSMSG or *STSMSG – *Status message display
I guess some users get real confused when they see those status messages blinking at them from line 24 of the display. It happens a lot during Query operations, and will also show up in custom code where the programmer is sending *status messages to keep the user informed.
But as the programmer, you may not want the user to know what the code is doing, so sometimes you want to hide your *status messages.
If *STSMSG is selected, the user will see status messages. If *NOSTSMSG is selected, the user will not see *status messages. If neither of these values is selected, the user will see *status messages.
Caveat: There are other avenues to control the display of *status messages: the system value QSTSMSG and the job attribute STSMSG.
*HLPFULL – Full screen help text
The i/OS has great HELP facilities. Cursor-sensitive HELP text is available on all IBM displays, and IBM and 3rd party vendors have provided great tools to easily build HELP text for your own application screens.
When you use the F1=HELP key, you typically get a limited help text window, which you can then scroll through to view the entire help text.
The *HLPFULL user option changes that windowed help text to cover the entire screen instead of a fraction of the screen. So *HLPFULL means full screen help text. I like this user option.
*PRTMSG – Message on printing action
By turning on *PRTMSG for a user, they receive an interrupting message telling them when their report is done printing.
Thursday, September 4, 2008
How your credit card works:
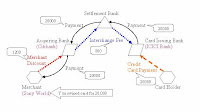
Priya: I want to buy a Sony digital camera costing Rs.20,000, but I don’t have any cash right now.
Raj: Why don’t you use your ICICI Bank credit card? Never heard them say? Hum Hain Na??
Priya: I am quite skeptic about using these cards. I pay using the card; get a bill after 30 days and pay after another 20 days. This is a maximum of 50 days interest free loan. Why does any bank do it?
If I borrow Rs.20,000 on personal loan at 11%.
Interest to be paid for 50 days = Rs. 20,000 * 11% * (50/365) = Rs. 301.40.
Here the bank is giving me a loan without interest when I use the credit card. Something is wrong somewhere!
Raj: Well? let me tell you how it works when you use your card to pay for the camera.
You present your ICICI Bank credit card a VISA card.
Sony World swipes your card on a machine provided by Citibank. Let’s call Citibank the acquirer bank and the process of Sony World swiping the card on that machine requesting authorization.
Citibank communicates with the card issuer.ICICI Bank through VISA Network to check if the card is valid and has the required credit limit.
ICICI Bank reviews and approves / declines which is communicated back to Sony World.
You sign a receipt called Sales Draft given by Citibank. This is the obligation on your part to pay the money to ICICI Bank. Data on this receipt can be captured electronically and transmitted.
At the end of day or at the end of some period Sony World chooses:
Sony World submits the receipt you signed to Citibank who pays Sony World the money. Sony World pays Citibank a fee called Merchant Discount. Let us say this is 6% of the sale value = 6% * 20,000 = Rs. 1200
Citibank sends the receipt electronically to a Visa data center which in turn sends it to ICICI Bank.
ICICI Bank transfers the money to a settlement bank which in turn transfers the funds to Citibank.
Citibank pays ICICI Bank an Interchange Fee of 4% of the sale value = 4% * 20,000 = Rs. 800
20 to 50 days later ICICI Bank gets the money from you? And you don’t pay the interest!!
Priya: Interesting! So Sony World pays more than the interest that I should have paid for the loan that I take. I, as a cardholder have the following benefits
1. Convenience of not having to carry cash.
2. Credit availability? Free of interest.
However what benefits does Sony World get for paying so much money? Isn’t it more profitable for them to take cash? They can save as much as Rs.1200.
Raj: Certainly. Some retail outlets offer you discounts if you pay by cash, don’t they?
However when you don’t count the money that you are spending, you tend to buy more! Cards encourage this? Called impulse purchase.
If you did not have access to credit, you would not have bought the camera this month? Or may be not any time soon either. By accepting cards, the merchant is actually extending you credit at the risk of the card issuer. He pays money to the banks to carry that risk.
Priya: So ICICI Bank uses this money to pay back to us when they announce 5% cash back. They insist that the Sales draft that I sign at the retailer should also be from ICICI Bank. This means they are saving on the Interchange Fee and also pay me a part of the Merchant Discount that they get.
Raj: Exactly! If you have noticed, ICICI Bank gives you the cash back in the next credit card statement. They keep the cash back money for a maximum of 60 days before passing on a part to you. This accrues them interest too.
Say if ICICI Bank earns an interest of 6% per annum for the cash they carry they get Rs.1000 * 6% * (60/365) = Rs. 10
That is not huge, but money nevertheless. And when you consider that almost everyone in this city shops with a credit card these days, it is a big sum.
Priya: And that also explains why banks tie up with petrol pumps like ICICI Bank has tied up with HPCL and I could re-fuel there without having to pay the fuel surcharge of 2.5%. The card issuer and the acquiring bank is the same and that saves interchange fees.
Raj: Good! You seem to have figured out how it all works! Let me summarize:
Priya: Toh ab shopping chalein?? Lets not miss the Shopping at the time of our celebration!
Wednesday, September 3, 2008
Executing Commands with system() function in RPG:
It's common to use the QCMDEXC when you want to execute a CL command from an RPG program. But you may find it more convenient to use a C runtime library function, system(), to accomplish the same purpose. The system() function will pass a command string to the command processor, without the need to pass the length of the command string, or any other parameters for that matter.
To call the system() function, you simply pass it a pointer to the command string. Here's the suggested prototype (along with some necessary H-specs):
/If Defined(*Crtbndrpg)
H Dftactgrp(*No)
/Endif
H Bnddir('QC2LE')
// ------------------------------------------------------- Prototypes
D GoCmd PR 10I 0 Extproc('system')
D CmdString * Value
D Options(*String)
The command string may be a variable, literal, named constant, or an expression. The following example shows a typical use:
/If Defined(*Crtbndrpg)
H Dftactgrp(*No)
/Endif
H Bnddir('QC2LE')
// ------------------------------------------------------- Prototypes
D GoCmd PR 10I 0 Extproc('system')
D CmdString * Value
D Options(*String)
D NullString
C -1
D Success C 0
D Returncode S 10I 0
D User S 10 Inz(*User) Varying
/Free
Returncode = Gocmd('WRKSPLF SELECT(' + User + ') OUTPUT(*PRINT)');
Select;
When Returncode = Success; // Command was successful
...
When Returncode = NullString; // Command string was null
...
Other;
// Command failed
...
Endsl;
/End-free
The return code will let you check for the success or failure of the system() function. The return code is zero if the command is successful, or 1 if the command fails. If you pass a null pointer to a string, system() returns -1, and the command processor is not called.
If the system() function fails (i.e., return code is 1), it sets a global variable _EXCP_MSGID with the CPF message ID. You can import this variable into your program to check for specific errors, as the
following example shows:
/If Defined(*Crtbndrpg)
H Dftactgrp(*No)
/Endif
H Bnddir('QC2LE')
// ------------------------------------------------------- Prototypes
D GoCmd PR 10I 0 Extproc('system')
D CmdString * Value
D Options(*String)
D NullString C -1
D Success C
0
D ObjectNotFound C 'CPF3142'
D ObjectInUse C 'CPF3156'
D Errmsgid S 7 Import('_EXCP_MSGID')
D Returncode S 10I 0
/Free
Returncode = Gocmd('DLTF MYLIB/MYFILE');
Select;
When Returncode = Success; // Command was successful
...
When Returncode = NullString; // Command string was null
...
When Errmsgid = ObjectNotFound; // CPF3142
...
When ErrMsgid = ObjectInUse; // CPF3156
...
Other; // Some other error
...
Endsl;
/End-free
To use the system() function, you must refer to binding directory QC2LE when compiling and/or binding the program. The above examples name QC2LE in the H-specs.
To call the system() function, you simply pass it a pointer to the command string. Here's the suggested prototype (along with some necessary H-specs):
/If Defined(*Crtbndrpg)
H Dftactgrp(*No)
/Endif
H Bnddir('QC2LE')
// ------------------------------------------------------- Prototypes
D GoCmd PR 10I 0 Extproc('system')
D CmdString * Value
D Options(*String)
The command string may be a variable, literal, named constant, or an expression. The following example shows a typical use:
/If Defined(*Crtbndrpg)
H Dftactgrp(*No)
/Endif
H Bnddir('QC2LE')
// ------------------------------------------------------- Prototypes
D GoCmd PR 10I 0 Extproc('system')
D CmdString * Value
D Options(*String)
D NullString
C -1
D Success C 0
D Returncode S 10I 0
D User S 10 Inz(*User) Varying
/Free
Returncode = Gocmd('WRKSPLF SELECT(' + User + ') OUTPUT(*PRINT)');
Select;
When Returncode = Success; // Command was successful
...
When Returncode = NullString; // Command string was null
...
Other;
// Command failed
...
Endsl;
/End-free
The return code will let you check for the success or failure of the system() function. The return code is zero if the command is successful, or 1 if the command fails. If you pass a null pointer to a string, system() returns -1, and the command processor is not called.
If the system() function fails (i.e., return code is 1), it sets a global variable _EXCP_MSGID with the CPF message ID. You can import this variable into your program to check for specific errors, as the
following example shows:
/If Defined(*Crtbndrpg)
H Dftactgrp(*No)
/Endif
H Bnddir('QC2LE')
// ------------------------------------------------------- Prototypes
D GoCmd PR 10I 0 Extproc('system')
D CmdString * Value
D Options(*String)
D NullString C -1
D Success C
0
D ObjectNotFound C 'CPF3142'
D ObjectInUse C 'CPF3156'
D Errmsgid S 7 Import('_EXCP_MSGID')
D Returncode S 10I 0
/Free
Returncode = Gocmd('DLTF MYLIB/MYFILE');
Select;
When Returncode = Success; // Command was successful
...
When Returncode = NullString; // Command string was null
...
When Errmsgid = ObjectNotFound; // CPF3142
...
When ErrMsgid = ObjectInUse; // CPF3156
...
Other; // Some other error
...
Endsl;
/End-free
To use the system() function, you must refer to binding directory QC2LE when compiling and/or binding the program. The above examples name QC2LE in the H-specs.
Handle errors in RPG like CL:
We can catch any type of exception in the RPG program by using MONITOR opcode, it is like the MONMSG of CLP. You can put any code between MONITOR and ENDMON opcodes, so that whatever error occurred in this range will be monitored. See the example below:
Example:
Declare an array like Arr with DIM(2) Declare 3 variables A, B and C with length 2,0.
The below code shows, how to monitor the runtime errors. The initial value of A and C is 0, initiate value of B is 11.
MONITOR
B DIV A
Arr(B) Dsply
ON-ERROR 0102
'Div by 0' Dsply
ON-ERROR 0121
'Index Err' Dsply
ON-ERROR
'Error' Dsply
ENDMON
Similar way specific errors can be captured and handled accordingly in RPG.
Example:
Declare an array like Arr with DIM(2) Declare 3 variables A, B and C with length 2,0.
The below code shows, how to monitor the runtime errors. The initial value of A and C is 0, initiate value of B is 11.
MONITOR
B DIV A
Arr(B) Dsply
ON-ERROR 0102
'Div by 0' Dsply
ON-ERROR 0121
'Index Err' Dsply
ON-ERROR
'Error' Dsply
ENDMON
Similar way specific errors can be captured and handled accordingly in RPG.
Monday, September 1, 2008
Vacation and Out of Office:
When you create a calendar entry (Event, Meeting, Reminder, etc) and choose the category Vacation...
when you save the document Lotus Notes automatically asks you if you want to set up the Out of Office feature.
If yes is pressed, then it will lead to the out of office set up and makes it easier.
when you save the document Lotus Notes automatically asks you if you want to set up the Out of Office feature.
If yes is pressed, then it will lead to the out of office set up and makes it easier.
Subscribe to:
Comments (Atom)